RESOURCES
Discover a wide range of human-centric cybersecurity resources sorted by type, including blogs, downloadable documents, videos, and past webinars. These informative materials provide valuable insights into the complexities of social engineering and offer expert recommendations to help you navigate these challenges.
- Whitepapers
- Videos
- Threat Intelligence
- Target Intelligence
- Podcasts
- On-Demand Webinars
- Customer Success Stories
- Blog
- In the News
Robert M. Lee, a recognized cybersecurity authority and CEO of Dragos, volunteered for a live hacking demonstration sponsored by Picnic....

Introduction The overwhelming prevalence of data breaches, exposed credentials, and the visibility of personal information underscores an urgent need for...

Scammers are getting smarter, and their tactics more sophisticated. They don’t just go after businesses or high-profile individuals anymore—they target...

There is campaign that is catching a lot of eyeballs right now as a write this blog. It’s a neat...

The first page of Google search results about you is a lot scarier than the dark web. But news organizations...

In this short interview by NewsByte.Tech published on HackerNoon, Matt answers the following questions: What is your company in 2–5...

Demo by Rachel Tobac at Elevate Festival In this video, Rachel Tobac, CEO of Social Proof Security and a member of Picnic’s...

Whether you are a cybersecurity professional, a product marketer, or a cybersecurity start-up founder, you will find this episode of...

Chief Information Security Officers (CISOs) are like sailing captains navigating their organizations through treacherous waters. The threats are ever-changing, and...

If you are a GRC professional or a Cybersecurity practitioner, you will find this episode of Picnic’s Podcast Interviews very...

We are thrilled to share with you a podcast interview with Lt. General (ret.) Charles Moore, also known as “Tuna.”...
Ben Andreas, VP of Managed Services at Picnic, offers a demo of the digital risk protection services (DRPS) platform to...

In an era where digital footprints are left everywhere, the recent unveiling of “The Mother of All Breaches” has sent...

In this session, recorded on 02/05/2024, Picnic and Scythe joined forces to offer a perspective on prevention that spans the...

Customer service centers, commonly known as call centers and IT support teams, often referred to as help desks, are becoming...

If you want to learn about Picnic and how we protect the human attack surface with digital risk protection services, this...

Jason Nations is the Director of Enterprise Security at OG&E. A seasoned IT and OT security executive, Jason highlights in...

LinkedIn has become an essential tool for professionals to network, share knowledge, and seek career opportunities. Yet, like any popular...

Howard Miller is the CIO at UCLA Anderson School of Management. He has been a Picnic customer for a few...

Download PDF Incident Name: Okta October 2023 Breach Date of Incident: 2nd – 18th October 2023 Summary: Okta, a well-known...

Download PDF Incident Name: 23andMe October 2023 Credential Stuffing Attack Date of Incident: October 2nd, 2023 Summary: 23andMe is a...

Brent Baker is the Executive Vice President of Information Technology at Rosen’s Diversified (RDI), a conglomerate of businesses in the...

NIST CSF, MITRE ATT&CK, and HASP frameworks In today’s digital world, the ever-evolving landscape of cybersecurity threats poses significant challenges...

Download PDF Incident Name: Retool August 2023 Social Engineering Attack Date of Incident: August 27th, 2023 Summary: Retool, a popular...

Download PDF Incident Name: MGM Resorts International September 2023 Ransomware Attack Date of Incident: September 10th, 2023 Summary: On September...
Download PDF Incident Name: Kroll August 2023 SIM Swap Attack Date of Incident: August 19th, 2023 Summary: Kroll is a...

Download PDF Incident Name: Okta August 2023 Social Engineering Attack Advisory Date of Incident: August 2023 Summary: Okta, a provider...

Download PDF Incident Name: CoinsPaid Social Engineering Attack Date of Report: August 7th, 2023 Date of Incident: July 22nd, 2023 Summary:...

Social engineering attacks are one of the most commonly used methods for cyber criminals to gain access to sensitive data...

Download PDF Incident Name: Henry Ford Health Data Breach Date of Public Report: July 18th, 2023 Date of Incident: March...

44 Minutes of Cybersecurity Insights Picnic CEO Matt Polak joined Jeff Farinich, CISO of New American Funding, on an Audience 1st...
Cybercriminals are always looking for ways to exploit the exposed personal data of high-value targets to breach companies. High-value targets...

The importance of understanding and managing the human element in your organization’s security strategy cannot be overstated as the stakes...

The spotlight in the fight against cybercrime continues to be an often overlooked yet pivotal factor – the human element....

We all know that the cybersecurity vendor landscape is extensive and looks complex. Although there is a gap in cybersecurity...

We Got This Covered: Picnic Picnic CEO Matt Polak recently joined Tidal Cyber’s Chief Innovation Officer Frank Duff on the “We’ve Got...

Human vulnerabilities create risks to infrastructure and data, which impacts operational, legal, financial, and reputational risks. Picnic prioritizes the vulnerabilities...

As specialists in human attack surface protection, we at Picnic know all too well the importance of preventing the exploitation...

The Threat of the Human Attack Surface Picnic CEO Matt Polak shares practical steps that businesses can take to protect themselves...

Social engineers collect intelligence on human targets to develop paths for attack and compromise. Picnic’s platform emulates this external, human...

The exploitation of human attack surface data and a crucial intelligence gap According to Verizon’s 2022 DBIR report, stolen passwords...

Download PDF Incident Name: Kodi February 2023 Data Breach Date of Public Report: April 8th, 2023 Date of Incident: February...

Social engineers collect intelligence on human targets to develop paths for attack and compromise. Picnic’s platform emulates this external, human...

Threat actors leverage exposed credentials, including passwords associated with employee and contractor personal accounts, in order to power credential stuffing...

Did you know credential compromise was the single largest source of breaches last year?* That’s why incorporating credential-stuffing security practices...

Download PDF Incident Name: Activision December 2022 Social Engineering Attack and Data Breach Date of Public Report: February 27th, 2023...

Webinar with Scott Goodhart, CISO Emeritus We talk with Scott Goodhart, CISO Emeritus, on the importance of knowing your human...

Most cybersecurity whitepapers start with a scary anecdote, a statistic on annual losses in the billions, some specifics on hard-hit...

Compromised employee credentials are a major threat to any organization’s cyber security. According to Verizon’s 2022 Data Breach Investigation Report,...

Download PDF Incident Name: Coinbase Social Engineering Attack Date of Incident: February 5th, 2023 Summary: Coinbase is an American cryptocurrency...

Download PDF Incident Name: Reddit Feb 2023 Social Engineering Attack and Data Breach Date of Incident: February 5th, 2023 Summary:...

Webinar with Dr. Max Kilger We talk with Dr. Max Kilger, Director of the Data Analytics Program and Associate Professor...

Download PDF Incident Name: Riot Games Jan 2023 Date of Incident: January 20th, 2023 Summary: Riot Games is an American video game developer...

Written by Karen Walsh Phishing scams and other social engineering attacks work because cybercriminals use people’s digital footprints against them....

Cybercriminals do what they do for money. According to the 2022 Data Breach Investigations Report, 96% of data breaches were...

What you’ll learn: What social engineering is Why social engineering matters Which organizations should be concerned Which individuals should be...
The Role of OSINT in social engineering and how to manage your human attack surface Picnic CEO Matt Polak recently joined award-winning...

Social engineers collect intelligence on human targets to develop identity paths for attack and compromise. Picnic emulates this external, human...

Every day, people follow a set of digital routines. Some people read the news online while drinking their morning coffee....

Picnic is excited to be featured on Startup to Follow’s list of the top startups of 2022! Check out their...

Webinar with Jim Routh In this webinar, we talk with Jim Routh, a former CSO and CISO, and current board member, advisor,...

Exploitation through easily accessible sensitive personal information is the single largest threat to companies and their people today. It’s how...
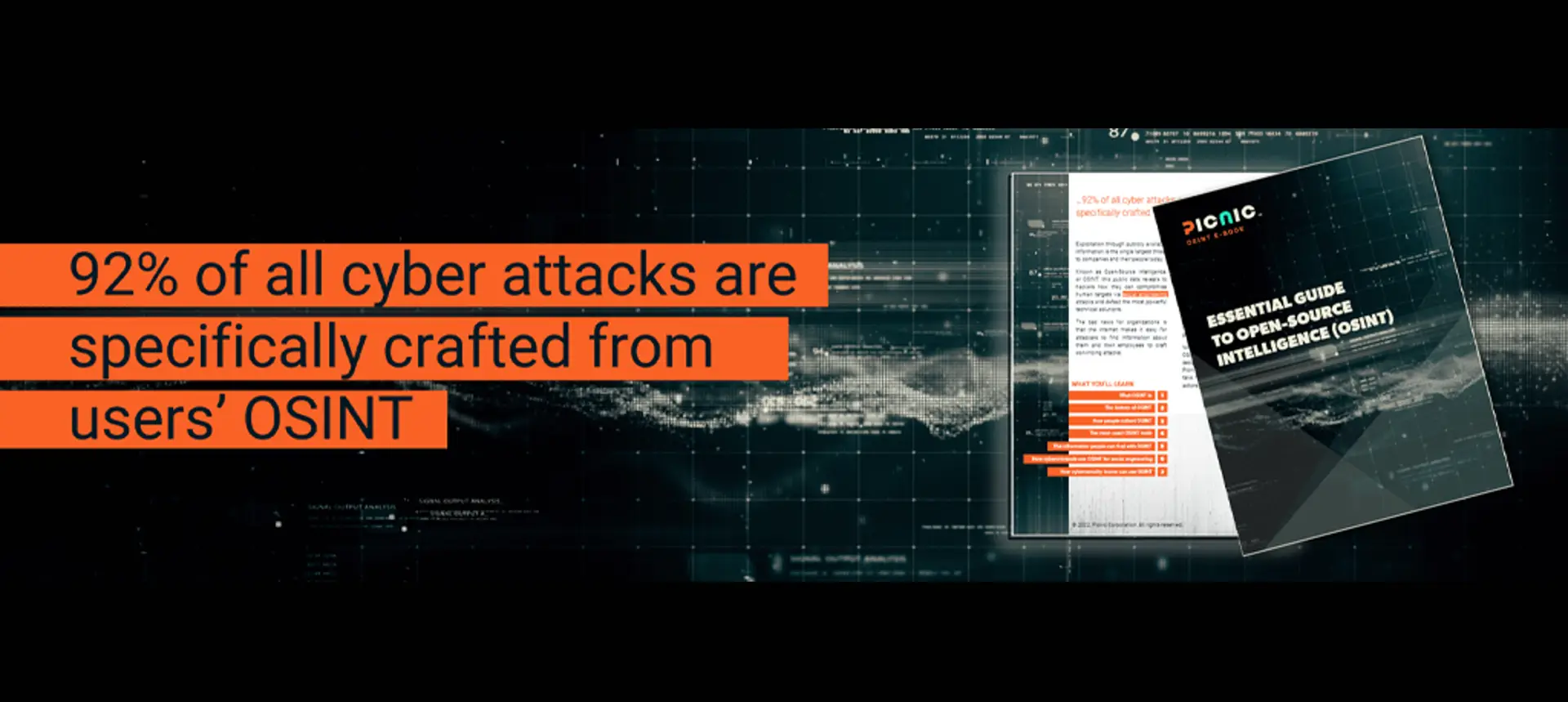
DOWNLOAD E-BOOK Exploitation through publicly available information is the single largest threat to companies and their people today. Known as...

Picnic Corporation founder and CEO Matt Polak discusses social engineering with analyst John Donegan. Among other topics, Polak covers the...

Protecting People and Companies from Social Engineering Attacks Picnic is a cybersecurity firm going after an aspect of risk that the...
Security Guy TV on how Picnic helps organizations see and remediate human risk beyond the corporate firewall Picnic CEO Matt...

SANS Cyber Solutions Fest ’22 Webinar with Jim Somborovich, Cybersecurity Leader and Veteran (USMC) SOC teams have historically not had...

SANS Blue Team Summit ’22 Webinar with Manit Sahib, Picnic Director of Global Threat Intelligence More than 90% of all...

Webinar with Robert M. Lee, Dragos Founder and CEO As traditional infrastructure has become sufficiently hardened, hackers have turned to...

Social media account takeover has exploded over the past year. Picnic’s own CEO Matt Polak weighed in on the social...

SANS First Look Webcast with Matt Polak, Picnic Founder and CE0 An attacker needs very little other than open source...

Hackers today use our exposed personal data against us. More than 90% of the time, cyberattacks are specifically crafted from...

Summary As the rising tide of social engineering attacks evolve in frequency and complexity, organizations are beginning to prioritize solutions...

Picnic Protects Your Company from Social Engineers What the company does Picnic is a cybersecurity firm that proactively protects people...

In the fourth episode of RedTeam Raw, Picnic’s Director of Global Intelligence, Manit Sahib, sits down with Dhruv Bisani, the Head...

The following insight was written by Andres Holzer-Torres and adapted by the hatchpad team. Andres is currently the Technical Team Lead...

In the third episode of RedTeam Raw, Picnic’s Director of Global Intelligence, Manit Sahib, sits down with experienced penetration tester, ethical...

In the second episode of RedTeam Raw, Picnic’s Director of Global Intelligence, Manit Sahib, sits down with certified SANS instructor, author,...

Picnic’s own VP of Engineering, Michael Hans, joined the discussion on “Stealth Startups” in the latest episode of ‘The Pair...

In the very first episode, Picnic’s own Director of Global Intelligence, Manit Sahib, talks with InfoSec legend Marcello Salvati, most...
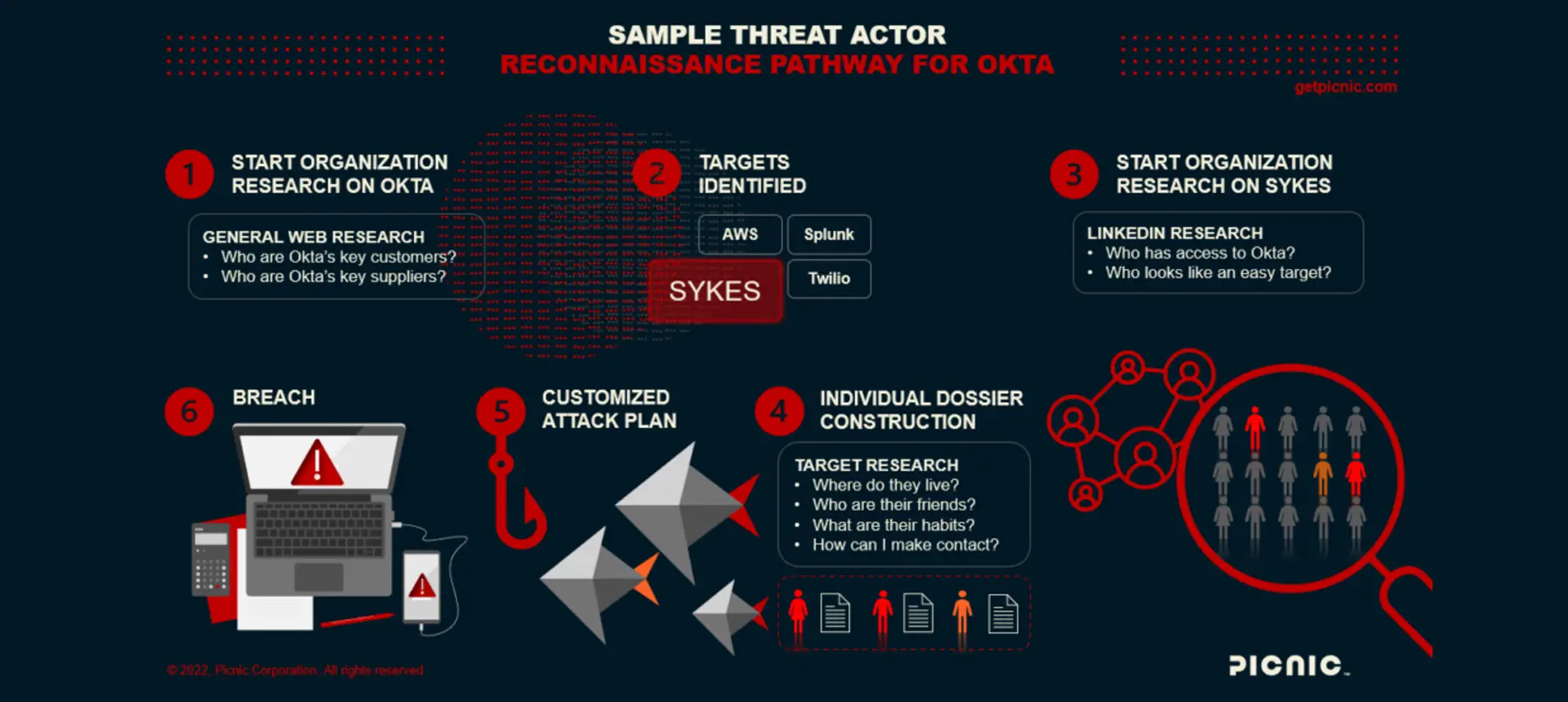
By Matt Polak, CEO of Picnic Two weeks ago, at a closed meeting of cyber leaders focused on emerging threats, the...

By Matt Polak, CEO of Picnic Cyber threat intelligence indicates that there is a high probability of digital retaliation against...

Using social media is, without a doubt, one of the most popular online activities that internet users engage in. Businesses...

How much data is produced every day? A quick Google search will tell you the current estimate stands at 2.5...

People’s perceptions have changed. Not so long ago we thought nothing of kids playing outside all day alone, unchaperoned visits...

I recently purchased a greenhouse from a well-known catalogue retailer – now I’m swamped with Google and Facebook ads for...

We all enjoy life in the digital age and the Internet provides us connectivity, efficiency and fun. By submitting some...

Cybersecurity has traditionally been seen as a job for IT departments – and most employees assume that cybersecurity is simply...

It is understandable that, when cybercrime happens to you, you can feel like you were targeted. And you certainly might...

Social engineering cyber-attacks have rocketed to the forefront of cyber-security risk and have wreaked havoc on large and small companies...

Ransomware is a form of malicious cyberattack that uses malware to encrypt the files and data on your computer or...

Everyone is familiar with the case in which the proverbial “little old lady” is duped out of her life savings...

Cyber fraud is lurking everywhere across the internet and one of the most effective tactics on victims is “phishing.” Phishing...

Would a company send me that? We’ve all heard of a phishing email. If you haven’t heard of a phishing...
Get started today
Move beyond the corporate perimeter to reduce human risk and proactively safeguard against cyber threats with zero effort.