The spotlight in the fight against cybercrime continues to be an often overlooked yet pivotal factor – the human element. A profound understanding of this dimension is vital for safeguarding digital ecosystems, and the recently published 2023 Verizon Data Breach Investigations Report (DBIR) offers eye-opening insights into this arena. In this blog, we unpack the key findings of the report, and correlate them with research conducted by Picnic’s Global Threat Intelligence team.
Let’s dive right into it. A startling statistic from the report suggests that social engineering attacks are not only becoming increasingly prevalent, but they’re also becoming exceedingly profitable for cybercriminals. Business Email Compromise (BEC) attacks, a particularly insidious subset of pretexting attacks, have nearly doubled across all incident datasets. These now account for over 50% of incidents within the social engineering pattern, underscoring the persuasive power wielded by cybercriminals.
A notable 74% of all breaches recorded in the report implicated the human element. 50% of all social engineering attacks were pretexting incidents—nearly double last year’s total. Whether through errors, privilege misuse, exposed or stolen credentials, or succumbing to social engineering, people have been inadvertently paving the way for security breaches. The statistic shows that proactively addressing and protecting the human element is integral to an organization’s defense strategy. And yet it only takes a few key individuals with lapses of judgment or a few exposed credentials for the attackers to bypass the most advanced security controls and the most cyber-aware cultures.
74% of all breaches recorded in the 2023 Verizon DBIR implicated the human element
Gaining access to an organization’s digital infrastructure remains a persistent challenge, and cybercriminals have adopted three primary methods: stolen credentials, social engineering, and exploiting vulnerabilities. This triad of attack vectors presents a multifaceted challenge that underscores the necessity of rigorous security protocols, continuous threat exposure monitoring, and timely patching of vulnerabilities, especially human vulnerabilities.
The 2023 Verizon DBIR underscores the increasing complexity and sophistication of the cyber threat landscape. It unequivocally points out the central role played by the human element and highlights the urgency of augmenting technical safeguards with a strong human-centric approach. Cybersecurity education and fostering a culture of vigilance within organizations can help in building resilient defenses against these evolving threats, but it is clearly not enough to prevent successful attacks.
Picnic’s Global Threat Intelligence findings during the first half of 2023
During the first half of 2023, Picnic’s Global Threat Intelligence team researched 29 high-profile breaches and analyzed their pre-attack and attack pathways. It is important to note the challenges the team faces when investigating a breach. Victim organizations do not always disclose information that helps with attribution related to initial access techniques. When it comes to social engineering attacks, it gets even more opaque; most companies don’t want to disclose that the human element played a big role in the breach. Therefore, our research was conducted using open source intelligence (OSINT) and with a focus on the most noteworthy breaches this year so far, when victim organizations were as transparent as they wanted to be.
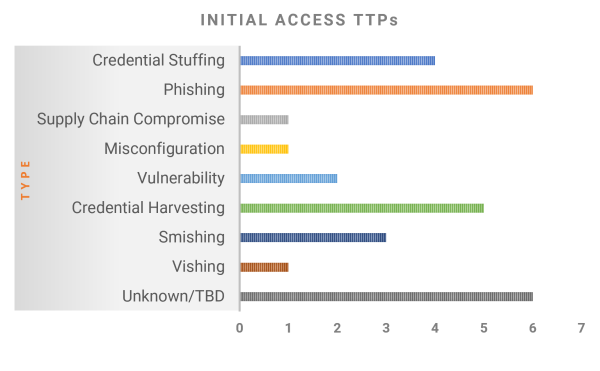
Unsurprisingly, phishing-related techniques were used in around half of the attacks we investigated, often coupled with an exploit and credential harvesting info stealer malware. Credential stuffing was the top initial access technique, where threat actors used stolen or breached credentials to access the victim organization’s resources. The healthcare industry was the most targeted, and phishing was the common initial access vector, where employee mailboxes and customer health data were compromised. These trends support our findings from our research on Twilio, Uber, and Mailchimp where phishing, credential harvesting, credential stuffing, and info stealer malware were key initial access vectors.
Phishing-related techniques were used in 50% of the attacks Picnic investigated
It is clear that the human element remains the key unsolved problem in cybersecurity. People and processes are exposed to external threats, not just infrastructure. Social engineering attack pathways need closer attention from cyber defenders. A highly accessible human attack surface is challenging to protect, but it is imperative that organizations take preventive and protective measures by reducing its size and by implementing a continuous threat exposure management program that accounts for it. Vulnerability management should move beyond just patching infrastructure and consider protecting people and processes as part of a layered defense-in-depth strategy. Investments in cyber defenses should better balance the weight between pre-attack and post-attack control capabilities, as most of it these days is biased towards detection and response vs. prevention and protection. Investments in cyber awareness training are necessary but useless if not coupled with threat intelligence prioritization and targeted human risk remediations.
As we grapple with these insights, one thing is clear: understanding and addressing the human element will be crucial in turning the tide against cybercrime. The 2023 Verizon DBIR and our own research serve as a stark reminder that in the digital world, we are all gatekeepers, and the human attack surface requires protection.
How Picnic helps protect the human attack surface
Picnic combines the unique technical capabilities of its technology platform, specialized knowledge of how attackers gain initial access, and proactive services to continuously protect and reduce the human attack surface of enterprises. The solution uses predictive data science and curated threat intelligence to uncover individual and corporate risks and predict the most likely pathways of compromise based on threat actors, their TTPs, and their target industries. These risks are then proactively mitigated via Picnic’s targeted remediations. These capabilities dramatically reduce organizational risk by continually protecting board members, executives, employees, and supply chain contractors that are at high risk of being targeted by threat actors. Picnic’s predictive intelligence prioritizes threat-informed defense to prevent and protect against operational interruption, financial loss, and brand and reputational damage that follow high-profile compromises.
Picnic’s solution utilizes the Human Attack Surface Protection (HASP) Framework, developed by Picnic in collaboration with cybersecurity leaders from different industries worldwide. The framework is a free resource and is available at: https://getpicnic.com/human-attack-surface-protection-framework.
If you would like to learn more about how we can protect your organization’s human attack surface, visit our HASP use case page or reach out to our team for a demo.
Become a Subscriber to receive timely articles on human-centric security issues:
