TECHNOLOGY INDUSTRY
Social engineering targets your team members and your business processes before it impacts the infrastructure you use, the technology you develop, and the customers you serve. Protect your human attack surface proactively without adding to your head count.
Picnic reduces individual risk. corporate risk. threat exposure. the human attack surface. the number of incidents. cybersecurity workload. cybersecurity operational costs. |
Most threat actors in the Technology sector target executives, employees, and contractors with privileged technical access to information technology. They also target front desk employees with privileged access to personally identifiable information. Help Desk employees, for example, are of high interest to an attacker. The threat actors’ main motive is financial; they aim to compromise organizations and their supply chains with whaling and ransomware attacks. Threat intelligence reveals that these cyber criminals rely on breached personal and work credential reuse, spear phishing, and supply chain vulnerabilities (human and technical) to execute their attack plan. But first, they conduct target reconnaissance to identify opportunities to attack and build dossiers of their intended victims by leveraging open source intelligence sources (OSINT) in the open, deep, and dark web, looking at professional and personal digital identities.
Picnic taps into the same OSINT sources threat actors use, and it operates its proprietary technology to:
- Analyze human risk
- Predict attack pathways
- Deliver prioritized remediations that harden your human attack surface to prevent social engineering attacks that can compromise your people and business
By partnering with Picnic to make your organization a tough target for attackers, you will see a quantifiable reduction in impersonation, spear phishing, and credential stuffing attacks.
Picnic delivers security outcomes

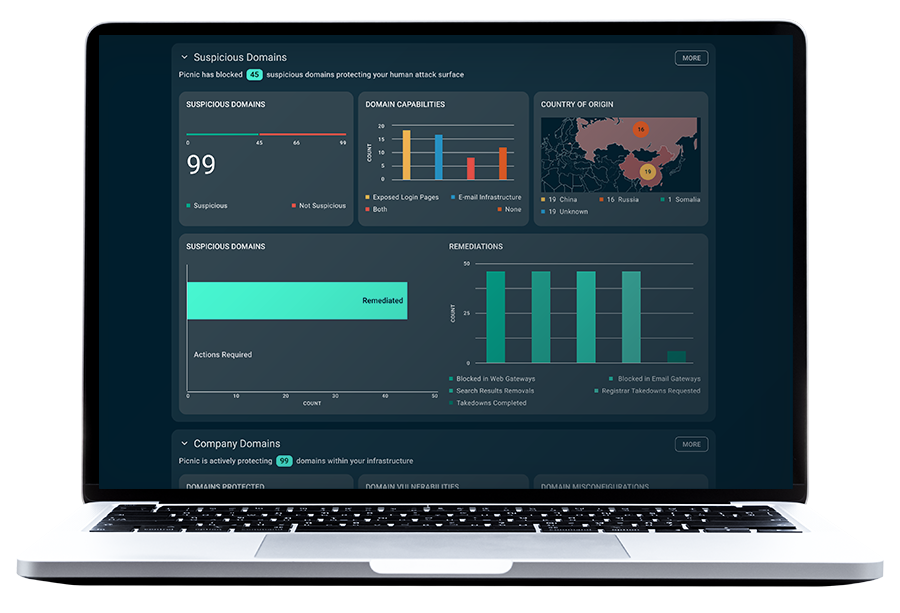
Why reduce human risk, and why now?
More than half of the population reuse the same password across multiple accounts.
Almost half of the population believes an email is safe if it contains familiar branding.
Ninety percent of all cyber attacks start with a phishing email.
Social engineering, web application attacks, and system intrusions account for seventy-seven percent of all cyber attacks in the technology industry.
Stop reacting. Start preempting.
A defense-in-depth strategy begins beyond traditional security controls to stop phishing, smishing, and vishing attacks before they start.
Explore our services
Most customers start protecting their human attack surface with Picnic High-Value Target DRPS and then expand coverage.
However, every organization has different priorities and goals. Tell us yours, and we will tailor a program that meets your needs.
Ready to get started?
Move beyond the corporate perimeter to reduce human risk and proactively safeguard against cyber threats with zero effort.
Resources
- All Posts
- Blog
- Customer Success Stories
- In the News
- On-Demand Webinars
- Podcasts
- Press Releases
- Target Intelligence
- Threat Intelligence
- Videos
- Whitepapers

If you want to learn about Picnic and how we protect the human attack surface with digital risk protection services, this is the webinar to watch. Matt Polak, CEO and founder

Howard Miller is the CIO at UCLA Anderson School of Management. He has been a Picnic customer for a few months and, in this video, shares the challenges Picnic helps

Social engineering attacks are one of the most commonly used methods for cyber criminals to gain access to sensitive data and information. Recent advances in generative AI have enabled threat