FREE 2-WEEK TRIAL
Visualize the social engineering threat exposure of up to 20 individuals and simulate the impact and fast time-to-value of Picnic remediations.
A frictionless proof-of-value at no cost to your organization.
How it works
This proof-of-value entails continuously visualizing and analyzing the social engineering threat exposure of twenty (20) individuals during the period of two weeks, predicting the impact of remediations, and delivering a comprehensive report for one (1) individual designated as a High-Value Target. This is performed by Picnic with near-zero customer involvement.
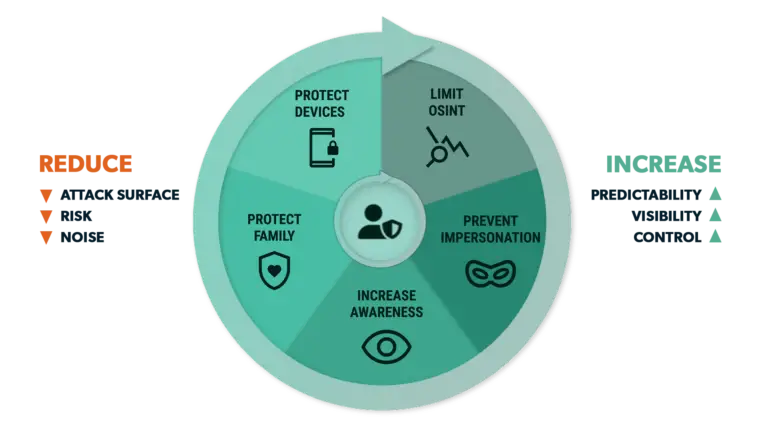
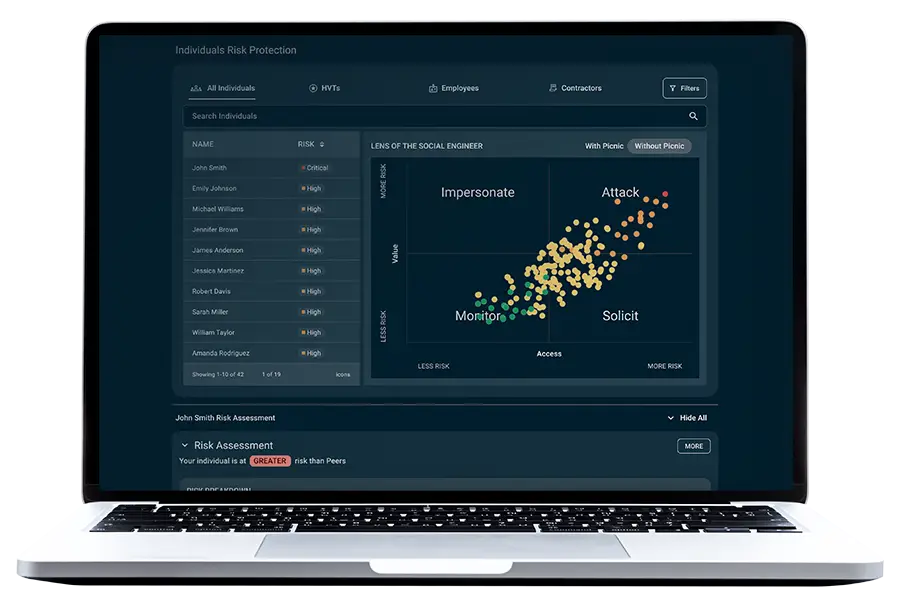
What we won't need
- No hardware deployment needed
- No endpoint agents installations are needed
- No integrations needed
- No access to your systems, infrastructure, or facilities is needed
What we will need
- Step 1: A kick-off meeting
- Step 2: A heads-up touchpoint halfway through the trial period
- Step 3: An impact briefing at the end of the trial period with the attendance of the designated High-Value Target and stakeholders
What you will see
- Exposed personal data harvestable by attackers
- Exposed breach data on the open, deep, and dark web
-
Individual threat exposure to:
- Brute force
- Credential stuffing
- Identity theft
- Password cracking
- Corporate and personal email spear phishing
- SMS spear phishing
- Social media spear phishing
What we will deliver
- Impact Briefing presentation with detailed risk and data analysis for the entire population
- Quantified risk detection of external human attack surface data for all enrolled users
- Simulated remediation of selected elements of the footprint for one (1) High-Value Target
- Detailed HVT Report that includes findings, analysis, remediations (simulated), and recommendations, with the opportunity to be reviewed ahead of the group presentation
- Access to the Picnic dashboard for up to three (3) corporate security users