ENERGY & UTILITIES INDUSTRY
Deny threat actors the opportunity to target the human attack surface with social engineering attacks that compromise business operations.
Picnic reduces individual risk. corporate risk. threat exposure. the human attack surface. the number of incidents. cybersecurity workload. cybersecurity operational costs. |
Most threat actors in the Energy and Utilities sector target executives, employees, and contractors with privileged technical access to operational technology (OT) and front desk employees with privileged access to information technology (IT). The main motivation of these criminal organizations is financial, and their main goal is to deploy and detonate ransomware payloads.
State-sponsored actors target the same “high-value” individuals but have a different mission: continuous reconnaissance and maintaining persistent access to critical infrastructure in preparation for any potential future conflict.
Threat actors operating in this sector rely on spear phishing and exploit infrastructure and supply chain vulnerabilities (human and technical) to execute their attack plan. But first, they conduct target reconnaissance to identify opportunities to attack and build dossiers of their intended victims by leveraging open source intelligence sources (OSINT) in the open, deep, and dark web, looking at professional and personal digital identities.
Picnic taps into the same OSINT sources hackers use, and it operates its proprietary technology to:
- Analyze human risk
- Predict attack pathways
- Deliver prioritized remediations that harden your human attack surface
Prevent social engineering attacks that can impact operations. By partnering with Picnic to make your organization a hard target for attackers, you will see a quantifiable reduction in impersonation, spear phishing, and credential stuffing attacks.
Picnic delivers security outcomes

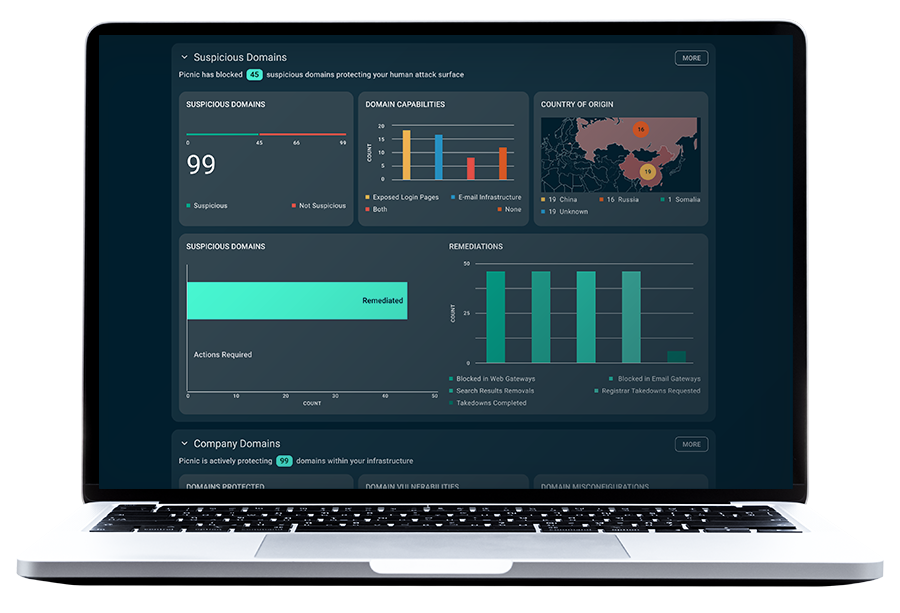
Why reduce human risk, and why now?
A third of all employees believe cybersecurity is not a top priority of theirs at work.
Nine out of ten cyber attacks start with a phishing email.
Almost half of the population believes an email is safe if it contains familiar branding.
The number of cyber attacks in the Energy and Utilities sector grew more than one hundred percent in the last year.
Stop reacting. Start preempting.
A defense-in-depth strategy begins beyond traditional security controls to stop phishing, smishing, and vishing attacks before they start.
Explore our services
Most customers start protecting their human attack surface with Picnic High-Value Target DRPS and then expand coverage.
However, every organization has different priorities and goals. Tell us yours, and we will tailor a program that meets your needs.
Ready to get started?
Move beyond the corporate perimeter to reduce human risk and proactively safeguard against cyber threats with zero effort.
Resources
- All Posts
- Blog
- Customer Success Stories
- In the News
- On-Demand Webinars
- Podcasts
- Press Releases
- Target Intelligence
- Threat Intelligence
- Videos
- Whitepapers

If you want to learn about Picnic and how we protect the human attack surface with digital risk protection services, this is the webinar to watch. Matt Polak, CEO and founder

Jason Nations is the Director of Enterprise Security at OG&E. A seasoned IT and OT security executive, Jason highlights in this video interview the high value and easy uptake and

LinkedIn has become an essential tool for professionals to network, share knowledge, and seek career opportunities. Yet, like any popular platform, it has become a fertile ground for threat actors