FINANCE
Accounts Payables teams are among the top targets of social engineering attacks. Picnic protects your people, your customers, and your supply chain, against fraud and impersonation attacks, ultimately preventing financial loss.
Picnic protects your people. your customers. your supply chain. your brand. your revenue. your bottom line. |
The main motivation of most threat actors, even some state-sponsored ones, is financial. Cybercriminals only need to find the opportunity to attack. To find it, they first conduct reconnaissance of the target organizations to understand the business cadence, supply chain, and high-value targets.
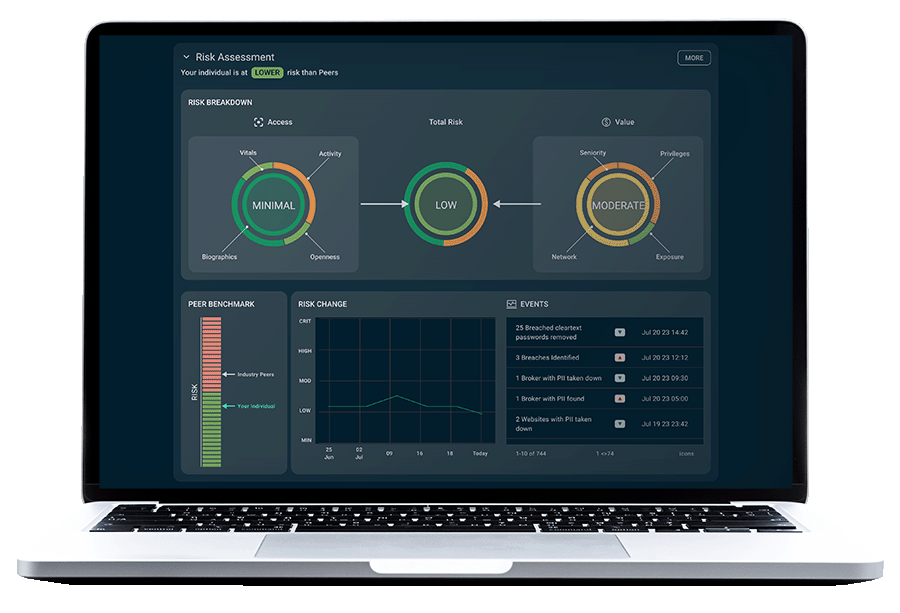
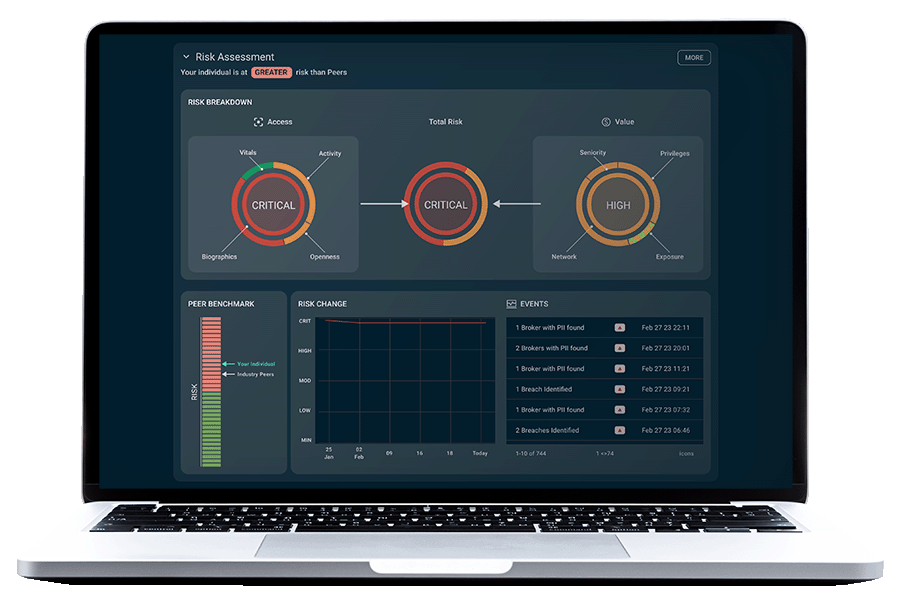
Picnic continuously looks at your human attack surface through the lens of an attacker, identifying employees with privileged financial and technical access, analyzing human risk, and predicting pathways to organizational compromise. The resulting risk visibility and awareness drive prioritized remediations that deny attackers the opportunities and the financial motivation to engineer an attack.
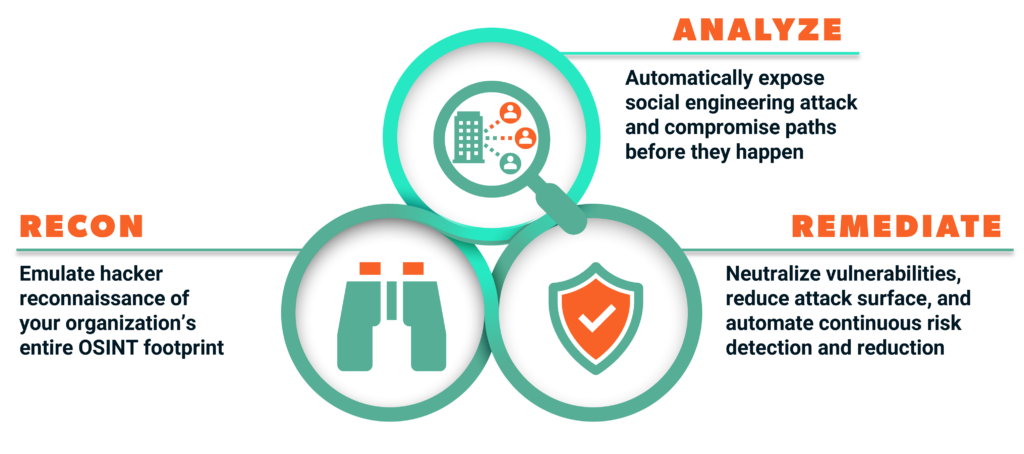
Picnic delivers security outcomes

Outcomes and benefits
Preempt the single largest source of breaches
Secure work and personal identities, disrupt attacker reconnaissance and resource development, and protect your human element, business processes, and infrastructure.
Safeguard your people
Protect your high-value targets, employees, and contractors from being targeted or exploited by threat actors.
Prioritize defenses
Fill a critical security gap with targeted remediations informed by relevant and timely threat intelligence mapped to your workforce.
Personalize security coaching
Tailor education to combat real-world threats with data-driven, risk-based social engineering training and advanced spear-phishing simulations.
Quantify and reduce human cyber risk
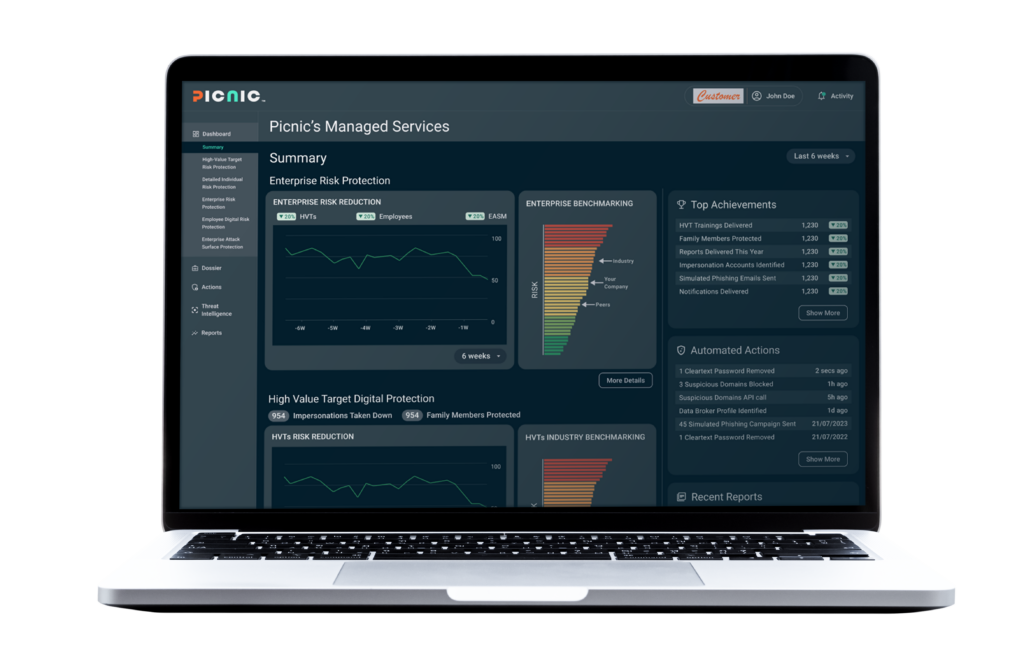
Know and communicate your progress with comparative scoring and reporting capabilities that facilitate sharing with stakeholders at all levels.
Service capabilities and deliverables
- Continuous, automated monitoring and protection of personal and professional digital footprint.
- 99% data broker removal, and we never give up on the stubborn 1%.
- Automated breached credential reuse protection for work and personal identities.
- 100% risk identification for email spoofing (work email and personal email) with remediation support.
- 100% identification and remediation of fraudulent social media accounts.
- 90% smishing reduction.
- Risk reports with comparative benchmarks.
- Real-time messaging about external footprint changes and related risk.
- Open, deep, and dark web monitoring for service accounts and domains.
- Protection against impersonation attacks using company email.
- Protection against phishing attacks targeting employees, customers, and suppliers.
- ... and more.
Explore our services
Most customers start protecting their human attack surface with Picnic High-Value Target DRPS and then expand coverage.
However, every organization has different priorities and goals. Tell us yours, and we will tailor a program that meets your needs.
Get started today
Move beyond the corporate perimeter to reduce human risk and proactively safeguard against cyber threats with zero effort.
Resources
- All Posts
- Blog
- Customer Success Stories
- In the News
- On-Demand Webinars
- Podcasts
- Press Releases
- Target Intelligence
- Threat Intelligence
- Videos
- Whitepapers

If you want to learn about Picnic and how we protect the human attack surface with digital risk protection services, this is the webinar to watch. Matt Polak, CEO and founder

Howard Miller is the CIO at UCLA Anderson School of Management. He has been a Picnic customer for a few months and, in this video, shares the challenges Picnic helps

Cybercriminals are always looking for ways to exploit the exposed personal data of high-value targets to breach companies. High-value targets (HVTs) are those individuals within an organization who have access