BREACHED CREDENTIAL REUSE PROTECTION FOR WORK AND PERSONAL IDENTITIES
Protect your organization against credential-stuffing attacks. Automatically prevent reuse within your organization of breached personal and corporate credentials. Picnic integrates with Microsoft Active Directory and with any identity provider via API to automatically block compromised passwords tied to your executives, employees, and contractors personal and work identities.
Breached Credential Reuse Protection prevents initial access by attackers. account takeover. identity compromise. data compromise. data loss. disruption to business operations. financial loss. reputational damage. |
When cyber defenders lack the automatic visibility and reuse prevention of corporate and personal clear-text credentials exposed in the open, deep, and dark web, they leave the door open to initial access via valid credentials.
Many employees use the same passwords across their work and personal applications. Threat actors connect personal and work identities and leverage exposed credentials, including passwords associated with employee and contractor personal accounts, for credential-stuffing attacks that provide initial access to targeted infrastructure. The 2024 X-Factor Threat Intelligence Index by IBM reported an increase of 71% yearly in the volume of attacks using valid credentials.
Picnic provides visibility and continuous monitoring of breach data to identify exposed corporate, personal, and third-party credentials and automatically prevents their reuse within the organization.
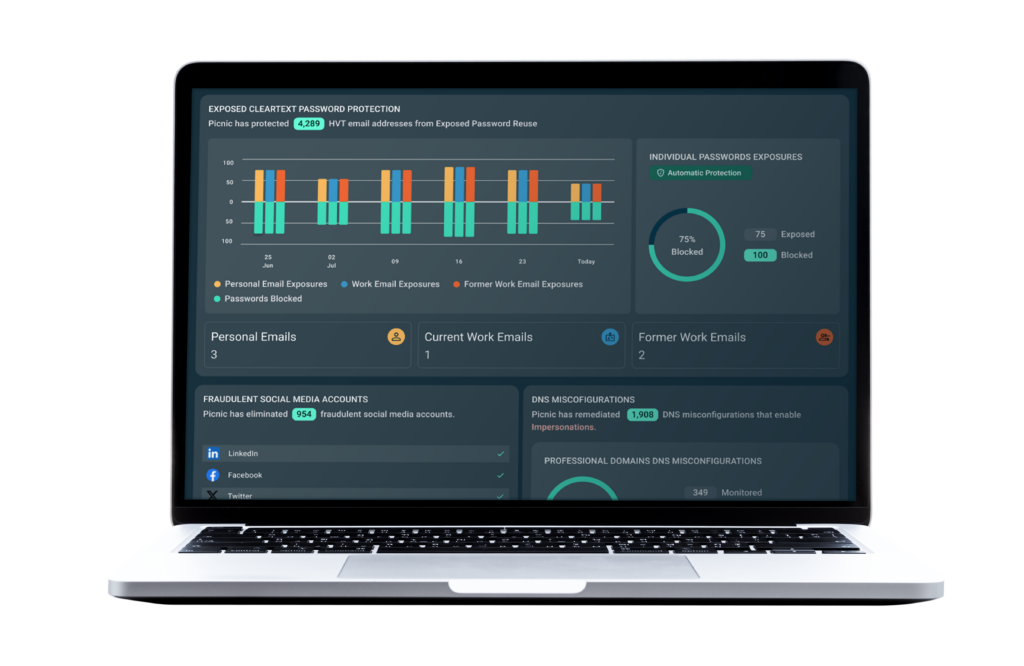
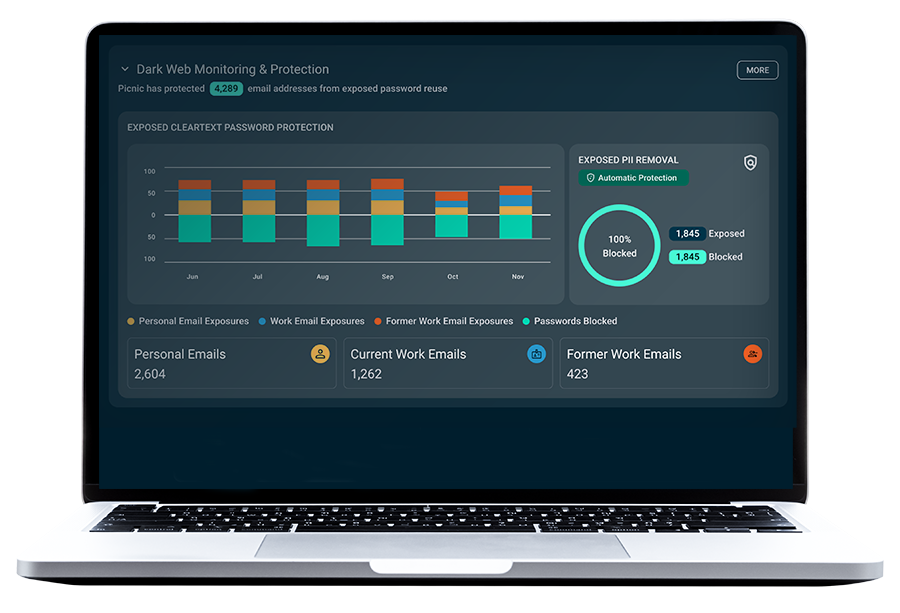
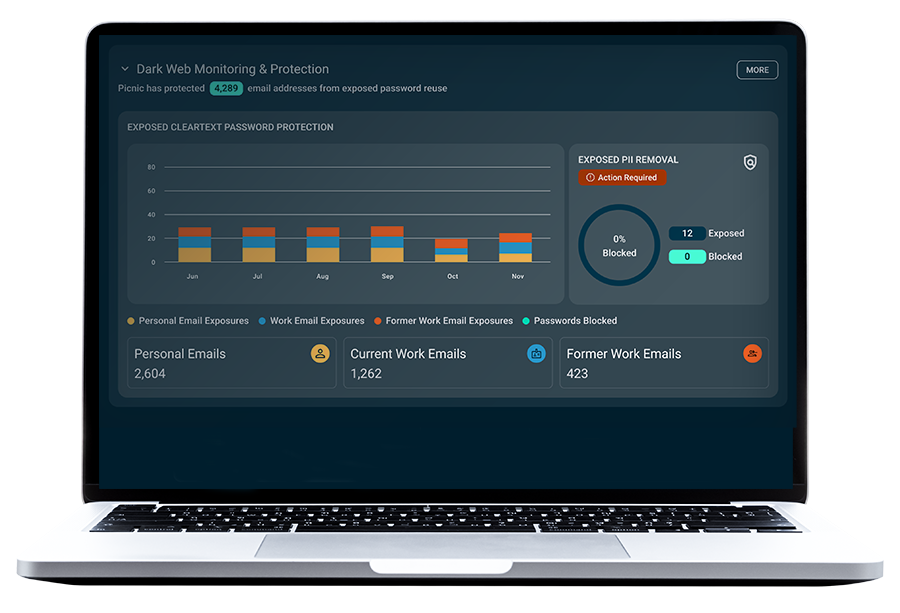
Picnic delivers security outcomes
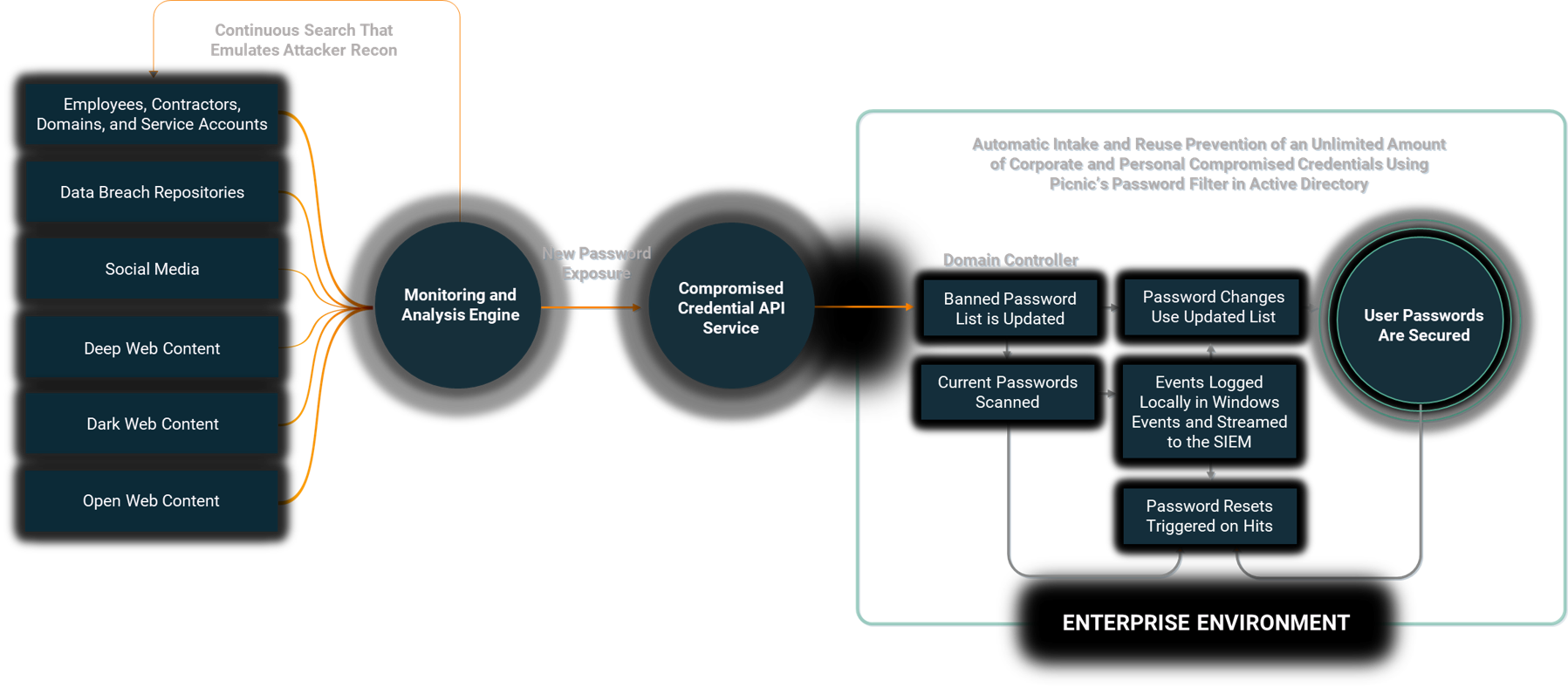
How it works
Features and capabilities
- Visualizes and reports on users at risk of credential compromise by dynamically tapping into multiple breach data repositories, social media, and the open, deep, and dark web.
- Dynamically feed a password filter to your IdP via a Picnic API or natively via an Active Directory plugin.
- Overcome Active Directory's limit of 1,000 passwords maximum and secure an entire population of users and service accounts.
- Integrates with any identity provider (IdP) via API, or on-prem and hybrid Active Directory environments.
- Trigger password resets and MFA for the users with surging risk of credential compromise and credential stuffing attacks.
- Events are streamed to your SIEM via Windows.
Outcomes and benefits
Preempt one of the largest source of breaches
Prevent initial access to your infrastructure by attackers using valid credentials by hardening your external attack surface against credential stuffing attacks.
Safeguard your people
Protect your high-value targets, employees, and contractors from account takeover (ATO) and improve identity security.
Quantify and reduce credential compromise risk
Know and communicate your progress with comparative scoring and reporting capabilities that facilitate sharing with stakeholders at all levels.
Get started today
Move beyond the corporate perimeter to reduce human risk and proactively safeguard against cyber threats with zero effort.
Explore more use cases
Most customers start protecting their human attack surface with Picnic High-Value Target DRPS and then expand coverage.
However, every organization has different priorities and goals. Tell us yours, and we will tailor a program that meets your needs.
Resources
- All Posts
- Blog
- Customer Success Stories
- In the News
- On-Demand Webinars
- Podcasts
- Press Releases
- Target Intelligence
- Threat Intelligence
- Videos
- Whitepapers

NIST CSF, MITRE ATT&CK, and HASP frameworks In today’s digital world, the ever-evolving landscape of cybersecurity threats poses significant challenges for organizations. Two major concerns are social engineering and credential

Did you know credential compromise was the single largest source of breaches last year?* That’s why incorporating credential-stuffing security practices into your organization’s security strategy is more crucial than ever.

Most cybersecurity whitepapers start with a scary anecdote, a statistic on annual losses in the billions, some specifics on hard-hit industries or recent attack variations, and then move on to