High-Value Target Digital Risk Protection Services
Protect your VIPs against social engineering attacks. Reduce organizational risk by 10% within the first month and by 65% in less than a year. Picnic's Managed DRPS delivers security outcomes fast by predicting human targets and attack pathways and prioritizing remediations.
High-Value Target DRPS reduces individual risk. corporate risk. threat exposure. the human attack surface. the number of incidents. cybersecurity workload. cybersecurity operational costs. |
Executives, board members, high-profile employees, individuals with privileged financial and technical access, and those who support them are all considered high-value targets (HVTs) by threat actors. Attackers leverage their exposed personally identifiable information for use in social engineering attacks to breach companies or defraud people.
Picnic offers a managed service that combines the unique technical capabilities of its technology platform, specialized knowledge of how attackers gain initial access, and proactive remediations to protect those individuals in your organization who are at high risk of being targeted or exploited by threat actors.
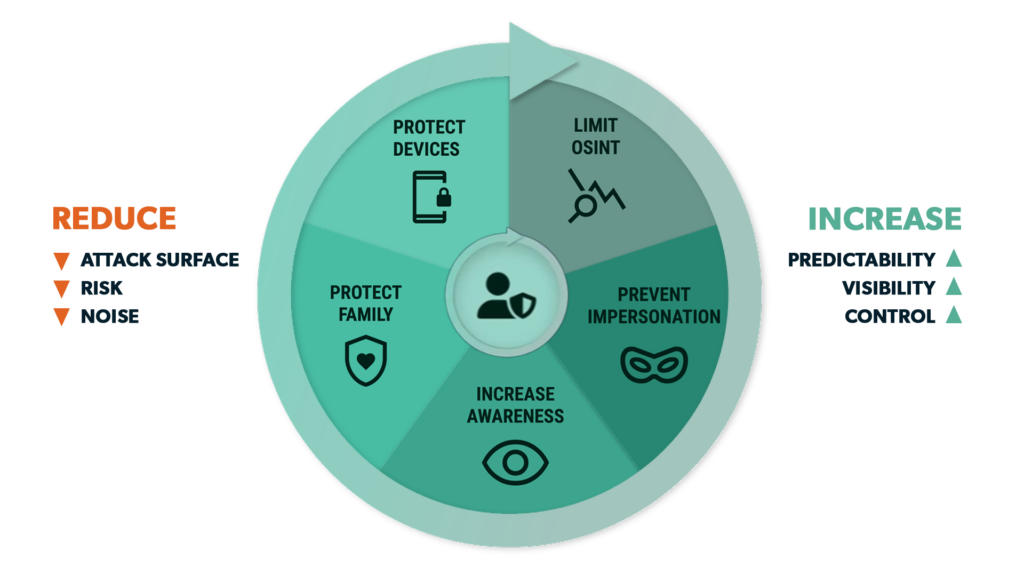

Picnic delivers security outcomes
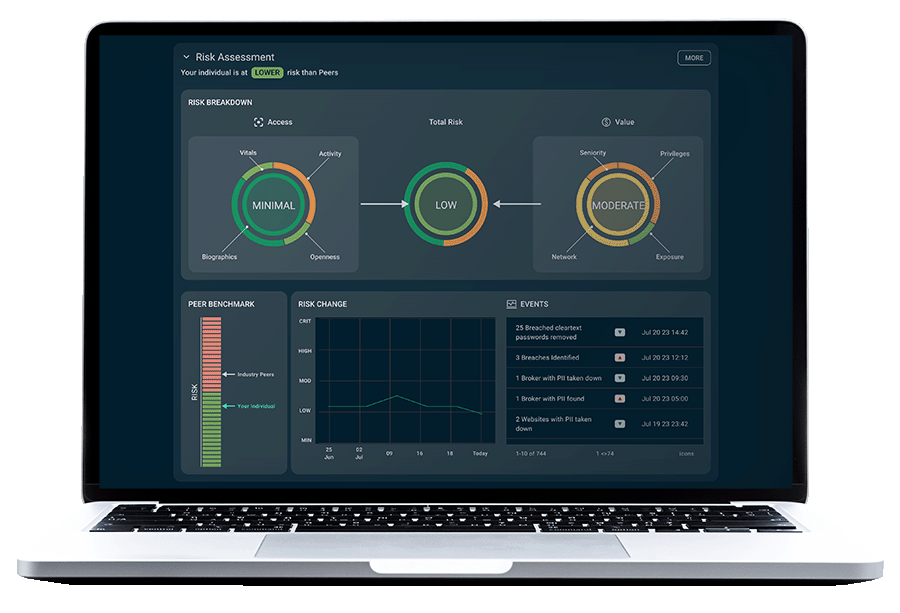
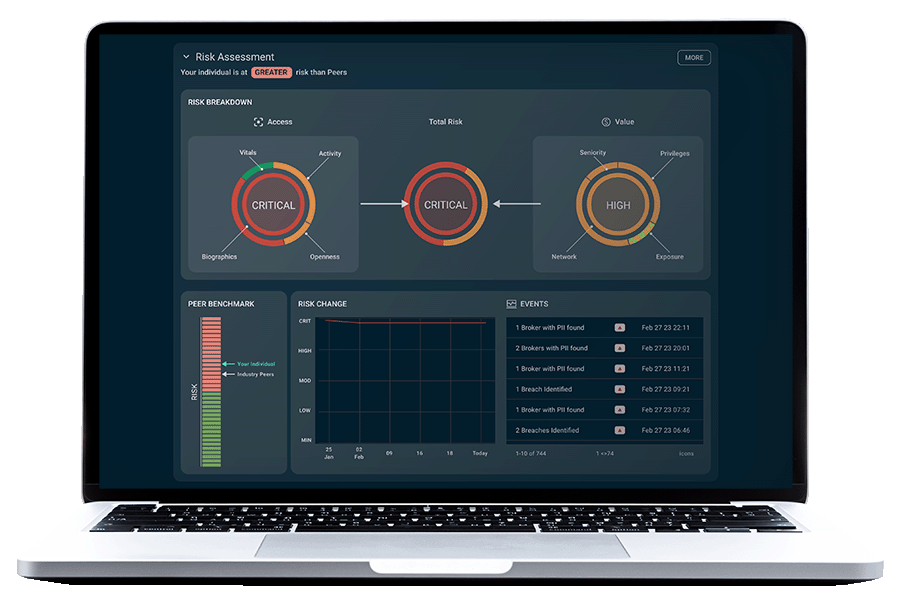
Outcomes and benefits
Preempt the single largest source of breaches
Secure work and personal identities, disrupt attacker reconnaissance and resource development, and protect your human element, business processes, and infrastructure.
Safeguard your people
Protect your high-value targets, employees, and contractors from being targeted or exploited by threat actors.
Prioritize defenses
Fill a critical security gap with targeted remediations informed by relevant and timely threat intelligence mapped to your workforce.
Personalize security coaching
Tailor education to combat real-world threats with data-driven, risk-based social engineering training and advanced spear-phishing simulations.
Quantify and reduce human cyber risk
Know and communicate your progress with comparative scoring and reporting capabilities that facilitate sharing with stakeholders at all levels.
Service capabilities and deliverables
- Continuous, automated monitoring and protection of personal and professional digital footprint.
- 99% data broker removal, and we never give up on the stubborn 1%.
- 100% risk identification for email spoofing (work email and personal email) with remediation support.
- 100% identification and remediation of fraudulent social media accounts.
- 90% smishing reduction, as reported by our HVTs.
- Annual, personalized HVT risk report.
- Real-time messaging about external footprint changes and related risk.
- Extended protection to family members.
- Personal EDR with ransomware, malware, and related threat protection.
- Advanced Red Team threat simulations.
Get started today
Move beyond the corporate perimeter to reduce human risk and proactively safeguard against cyber threats with zero effort.
Explore more use cases
Most customers start protecting their human attack surface with Picnic High-Value Target DRPS and then expand coverage.
However, every organization has different priorities and goals. Tell us yours, and we will tailor a program that meets your needs.
Resources
- All Posts
- Blog
- Customer Success Stories
- In the News
- On-Demand Webinars
- Press Releases
- Target Intelligence
- Threat Intelligence
- Videos
- Whitepapers

If you want to learn about Picnic and how we protect the human attack surface with digital risk protection services, this is the webinar to watch. Matt Polak, CEO and founder…

Howard Miller is the CIO at UCLA Anderson School of Management. He has been a Picnic customer for a few months and, in this video, shares the challenges Picnic helps…

Cybercriminals are always looking for ways to exploit the exposed personal data of high-value targets to breach companies. High-value targets (HVTs) are those individuals within an organization who have access…