Continuously neutralize digital exposure for Section 16 officers and their families.
DIGITAL VIP PROTECTION
The “digital exhaust” of your Section 16 officers and their families creates opportunities for threat actors and risks for protectees. Like camouflage in the jungle, having a clean digital footprint improves every aspect of operational security. Picnic continuously monitors and neutralizes digital exposure. Our proprietary technology proactively identifies, analyzes, and removes exposed personal data. Protectees and their families are, therefore, harder to track, target, deceive, impersonate, and coerce. We wield these digital superpowers on your behalf – there is no work for you to do.
Digital Exhaust
A complex security challenge for executive protection teams
Picnic leverages its staff's decades-long combined experience in human intelligence (HUMINT), threat intelligence, and cybersecurity operations to help organizations shift from a reactive stance focused on detection and response to a proactive stance focused on prediction and prevention.
We fully manage digital executive protection using proprietary technology to automatically and continuously reduce the unwanted and unnecessary digital footprints of executives, board members, and key employees, such as those with privileged access to secure facilities and business-critical systems. We augment our technology with a US-based team of digital warriors adept in finding and removing unwanted data about protectees and their families.

Picnic fosters privacy and operational security
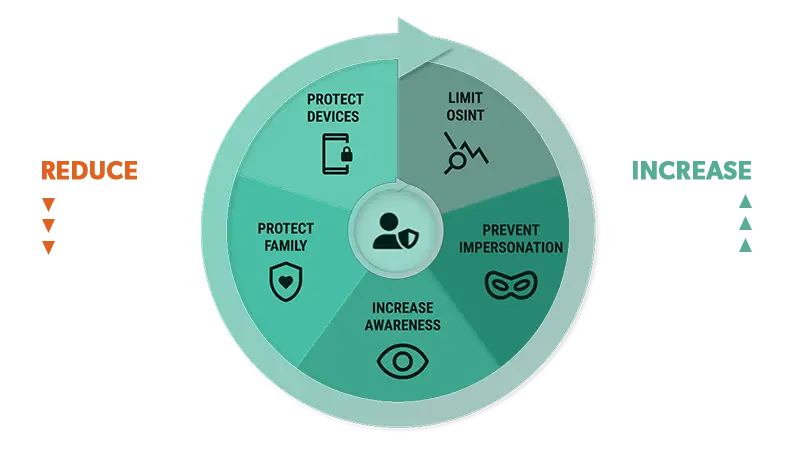
Balancing the need to publicly represent the brand vs. limiting available information to cybercriminals can be challenging for VIPs and security teams. Threat actors do not discriminate between personal and work identities when planning an attack against an organization. As a result, right-sizing the digital footprint of the executive team means continuously identifying and removing unwanted and unnecessary information available in the wild that attackers exploit. Picnic continuously identifies, analyzes, prioritizes, and remediates human risk, so you don’t have to.
Threat exposure protection by Picnic
- Continuous, automated monitoring and protection of personal and professional digital footprint.
- 99% data broker removal, and we never give up on the stubborn 1%.
- 100% blocking of breached credentials associated with work and personal identities, as well as service accounts
- 100% identification of email spoofing (work email and personal email) with remediation support
- 100% identification and remediation of fraudulent social media accounts
- 90% smishing reduction, as reported by our customers
- Risk reports with comparative benchmarks
- Real-time messaging about external footprint changes and related risk
- Extended protection to close associates and family members
- Personal EDR with ransomware, malware, and related threat protection
- Advanced red-teaming social engineering threat simulations
- ... and more.
Reporting on the impact
The Picnic Platform
Continuously analyzes and reports on individual and corporate risks and tracks the actions taken by our automation and our team to reduce them.
Online Dashboard
Enables you to gain prioritized social engineering threat exposure visibility while respecting the privacy of protected VIPs and their families.
Real-Time Alert Notifications
A fully customizable alert notifications engine powered by continuous open, deep, and dark web monitoring triggers automated alert notifications via e-mail and collaboration tools following predefined criteria.
Executive Reports & Briefings
Frequent confidential reports from Picnic delivered to you and protected VIPs drive relevant data-backed cyber awareness coaching to foster operational security improvements.
Interested in Digital VIP Protection?
Let's meet soon.
Choose an available date and time that’s convenient for you.