PROACTIVE SECURITY SOLUTIONS
Shift your cybersecurity to predictive prevention by supercharging your reactive controls with Picnic human risk intelligence.
HUMAN RISK API
Enrich your existing user metadata with individual user risk intelligence and exposure information without ingesting exposed PII.
While you can access user risk metadata and exposure information by logging into the Picnic dashboard and via reports, a REST API enables the seamless operationalization of that human risk intelligence without ingesting exposed PII. Injecting Picnic intelligence into your IdP, IAM, EDR, SIEM, SOAR, Email Security, and Cyber Awareness Training platforms via API supercharges your security controls and enables a human-centric cybersecurity strategy.
For API documentation, visit the Picnic Developer Portal
Picnic Human Risk API enables you to:
- Incorporate the human element into cybersecurity playbooks.
- Ingest human risk metadata for overall risk assessment and reporting.
- Identify users with recent cleartext password exposure to trigger password resets, MFA profile updates and/or security group assignment updates.
- Segment users by vulnerability to specific threat types, such as credential stuffing and SMS spear phishing, and design risk-triggered workflows based on those threats.
- Prioritize users for IAM authentication profile updates, security group assignments, cyber awareness training, phishing simulations, and red team targeting.
COMPROMISED CREDENTIAL API
Automatically and continuously protect your organization against compromised credential reuse.
Most employees reuse passwords from past jobs and personal accounts within their current work environment. Most do not know if their credentials were exposed in a breach, and threat actors can exploit this blind spot in your organization to conduct credential-stuffing attacks.
Picnic provides visibility and continuous monitoring of breach data to identify exposed corporate, personal, and third-party credentials and automatically prevents their reuse within the organization. A native integration with Microsoft Active Directory that bypasses the 1000 password limit is also available.
Picnic Compromised Credential API enables you to:
- Visualize and report on users at risk of credential compromise by dynamically tapping into multiple breach data repositories, social media, and the open, deep, and dark web.
- Dynamically feed a password filter to your IdP via a Picnic API or natively via an Active Directory plugin.
- Overcome Active Directory's limit of 1,000 passwords maximum and secure an entire population of users and service accounts.
- Integrate with any identity provider (IdP) via API, or on-prem and hybrid Active Directory environments.
- Trigger password resets and MFA for the users with surging risk of credential compromise and credential stuffing attacks.
- Stream events to your SIEM via Windows.
How it works
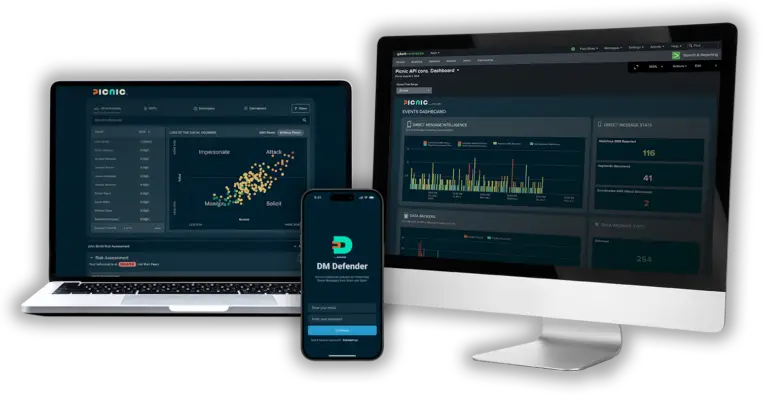
DM DEFENDER MOBILE APP (beta)
Anti-smishing protection & intelligence
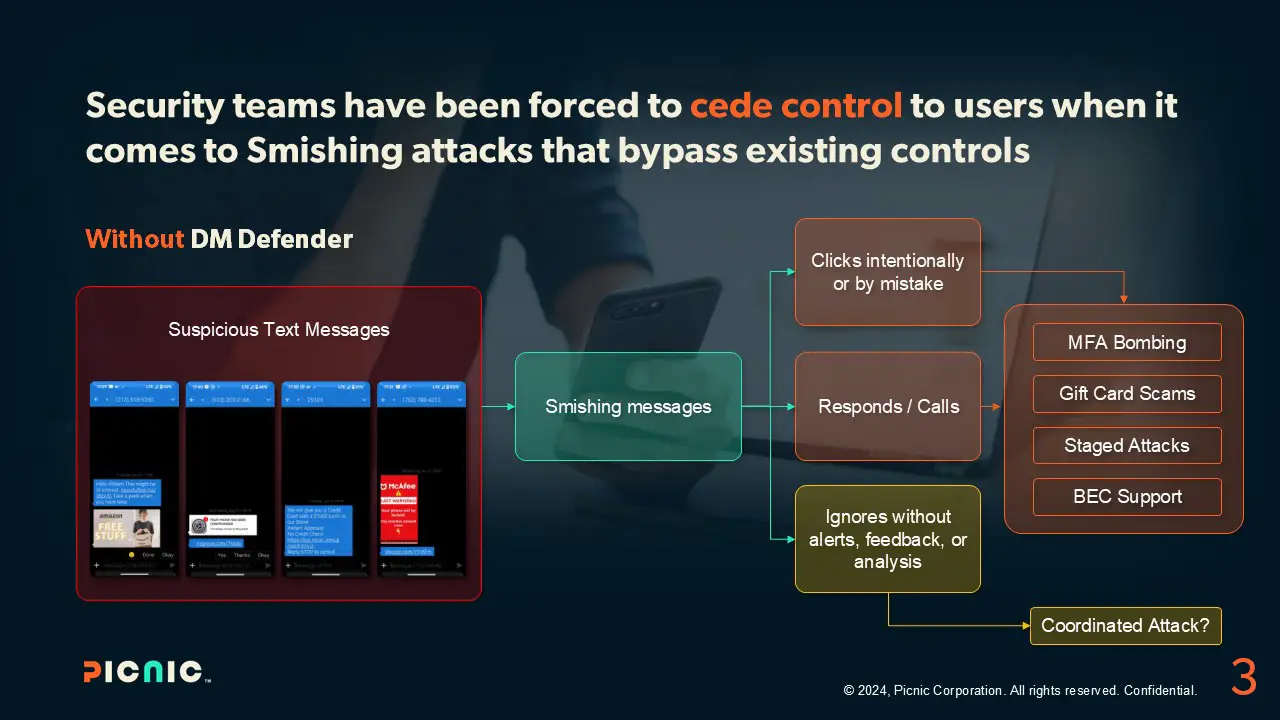
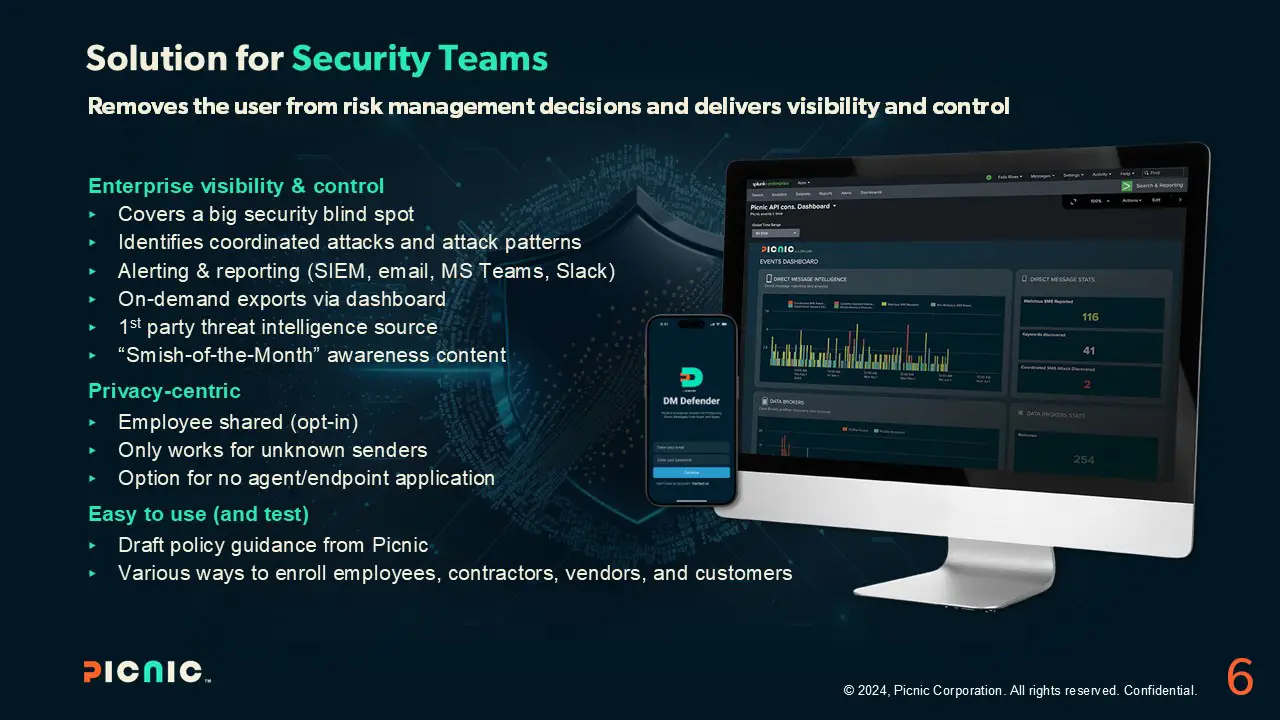
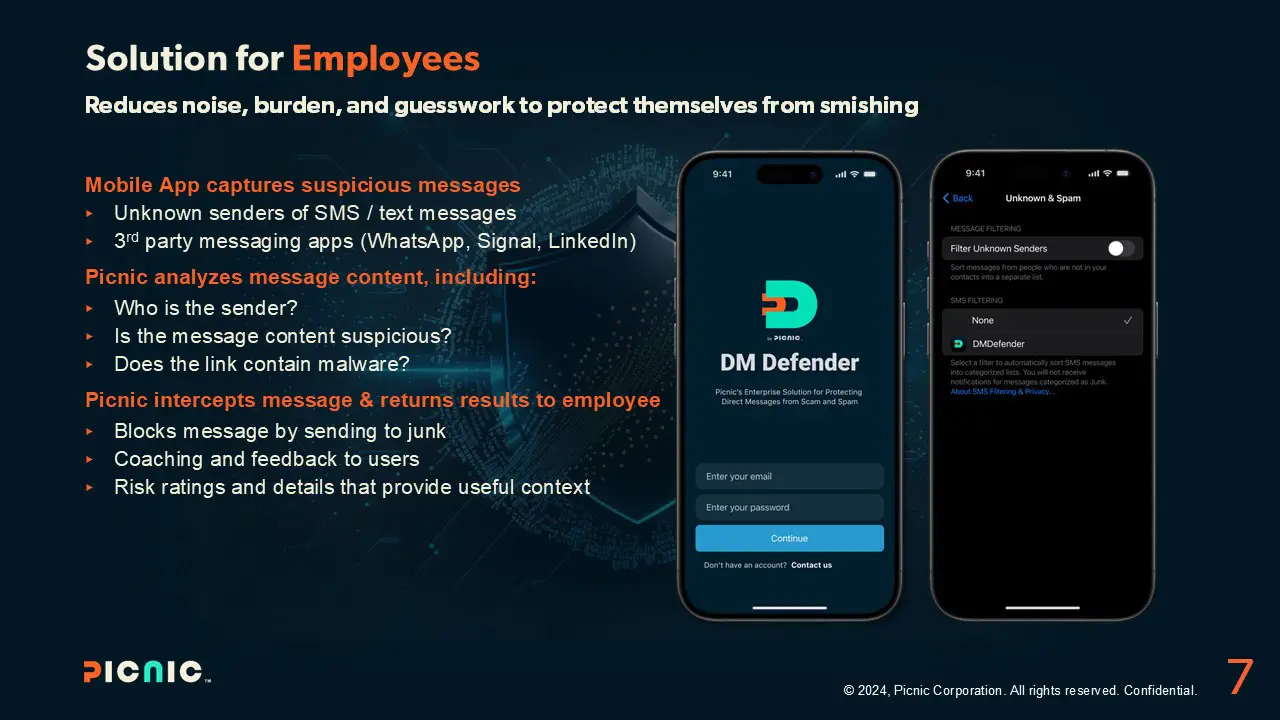
Security teams have been forced to cede control to users when it comes to smishing attacks that bypass existing controls. Besides the potential for real damage, there is a lack of visibility in detecting attack patterns and identifying coordinated attacks.
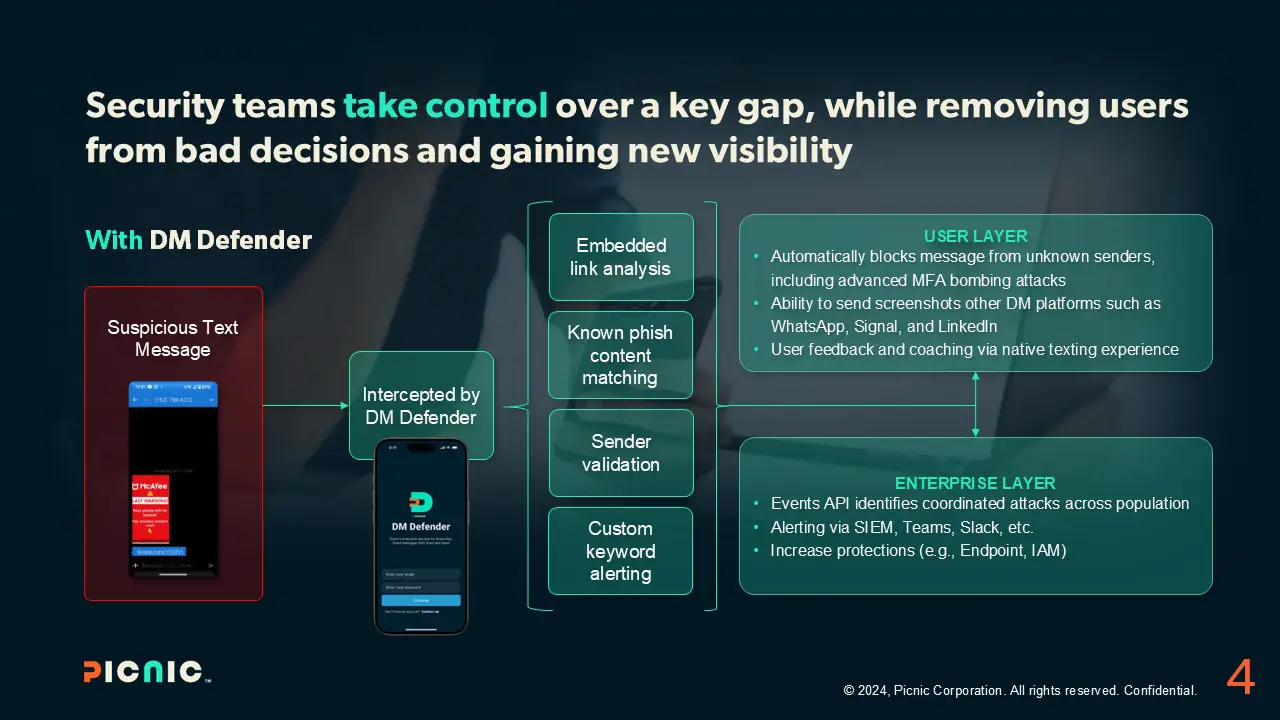
Picnic has developed the first-ever comprehensive anti-smishing and threat intelligence collection solution that enables Security teams to gain smishing visibility and control and prevent users from making bad security decisions. DM Defender is a component of the Picnic platform and integrates with your existing security stack to deliver intelligent protection.
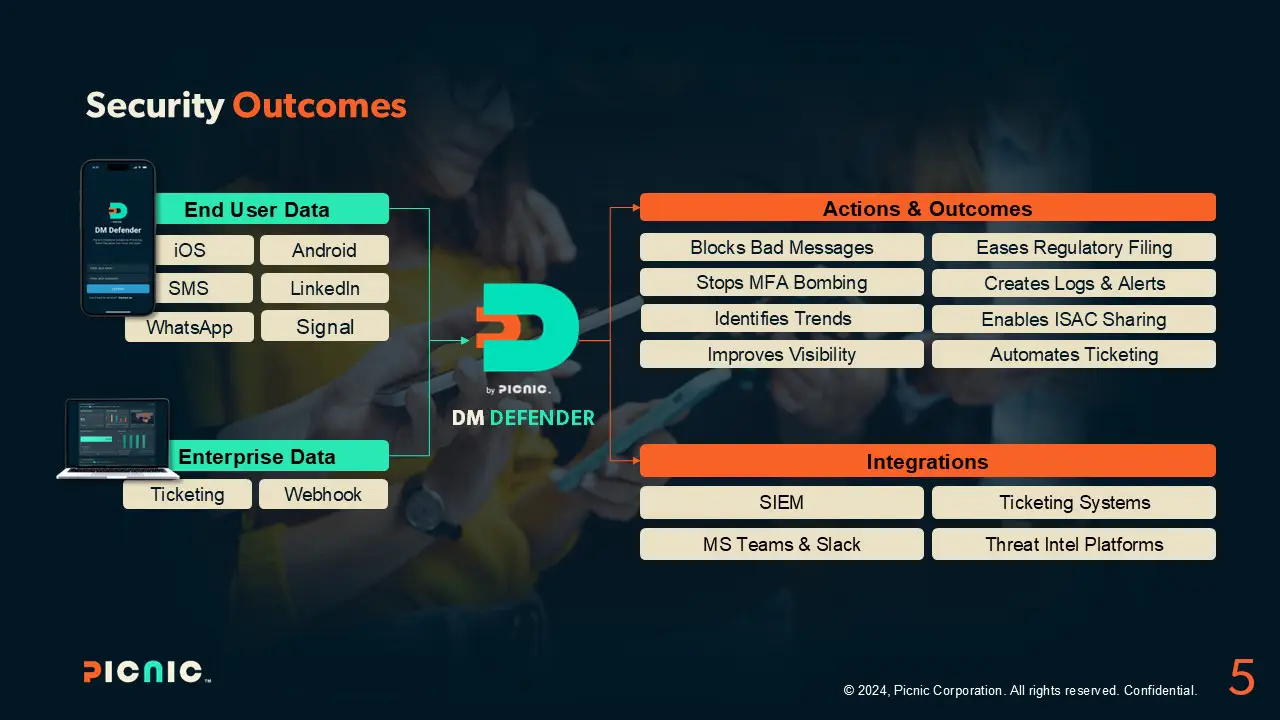
DM Defender enables you to:
- Block bad messages and stp MFA bombing.
- Improve visibility and identify trends.
- Ease regulatory filing.
- Create logs and alerts.
- Share with ISAC.
- Automate ticketing.
How it works



Start for Free
Picnic is the enterprise's alternative to consumer-grade PII removal services. See for yourself with a 2-week proof-of-value.