What you’ll learn:
- What social engineering is
- Why social engineering matters
- Which organizations should be concerned
- Which individuals should be concerned
- Why current solutions fail to stop attacks
- How to evaluate potential solutions
- How Picnic works and how it’s different
- How to protect your personal information to prevent social engineering
What is social engineering?
Social engineering is a term that refers to manipulating people for a particular end, either to get them to do something or to think a certain way. The technique uses psychology to “engineer” certain behaviors and outcomes. In a way, much of advertising is social engineering.
In the cyber world, social engineering is a method employed by attackers to bypass security controls by manipulating human targets. Social engineering includes a myriad of attacks, with some form of phishing being the most common, but they all have one common thread: they seek to trick targeted people into doing something by leveraging personal data about the target and their personal and professional networks.
Cybercriminals use social engineering to lure targets into handing over personal credentials, opening malicious files, wiring funds, or granting access to sensitive data. Nearly all cyber breaches today are the result of social engineering attacks on people, which give attackers an initial foothold from which they can compromise an organization further.

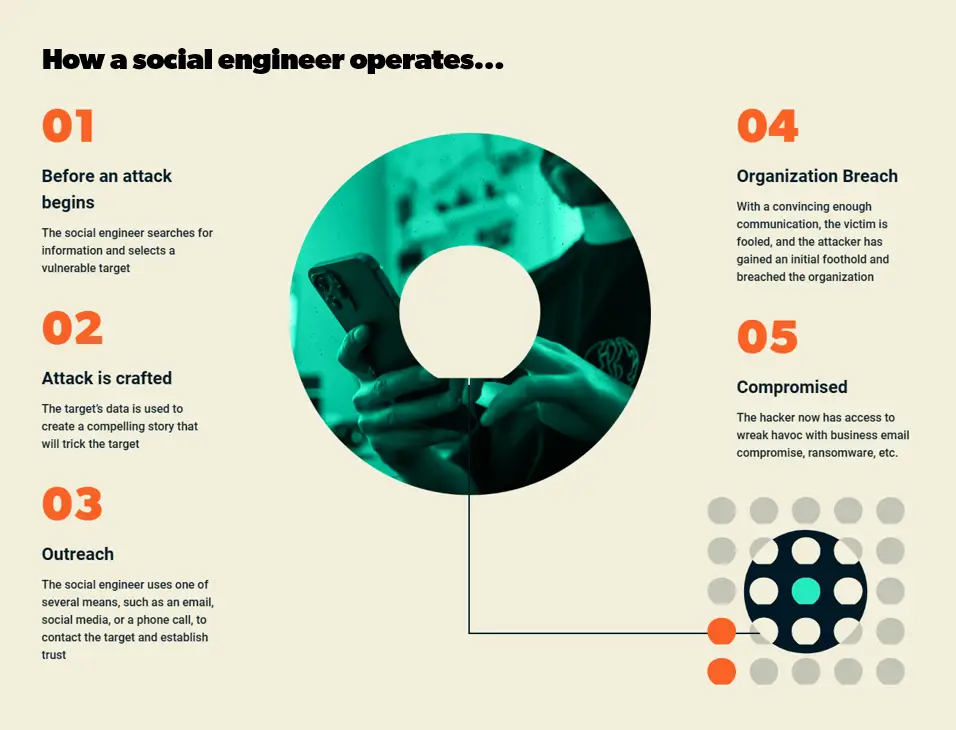
When planning to conduct a social engineering attack, hackers choose their human targets by scanning and analyzing the vast amount of information on people and organizations available online. This publicly available information is known as OSINT, or Open-Source-Intelligence, and it tells attackers who is a vulnerable and valuable target, how best to contact them, how to establish trust, and how ultimately to trick, coerce, or manipulate them.
Skilled social engineers use this information to craft appealing and effective—and at times irresistible—approaches to targeted victims. The approaches are often so personal and well-crafted that the target unwittingly gives the attacker the information needed to gain access to a system, take over an account, deploy ransomware or malware, steal that person’s identity, or engage in other types of fraud.
Why does social engineering matter?
Social engineering now fuels more than 90% of cyberattacks and has become the go-to method for hackers looking to breach organizations. Traditional cyber security tools have become so effective at preventing “old-school” breaches that cybercriminals now find it far easier—and more profitable—to use social engineering to fool users into divulging information that enables their attacks. By successfully targeting the person in the chair, hackers can defeat even the most powerful technical solutions, costing companies billions in losses each year. These attacks are not stopped by existing solutions because they sidestep traditional cybersecurity defenses, relying on employees’ access to systems rather than trying to break into the systems directly.
Social engineering has remained the problem that it is in large part because traditional cybersecurity has failed to address its root cause—publicly available information about people and organizations and their personal and professional networks (OSINT). The volume of detailed personal information available on most people and organizations online constitutes a virtual ocean of data that cybercriminals have learned to harness and exploit to select targets and craft social engineering campaigns.
Since all of us living in modern society have digital footprints, any individual or organization can be targeted in a social engineering attack. It is not a matter of if, but when. As the sophistication of the attacks continues to grow, so does the data that fuels them, and with defenses and training failing to keep up, social engineering is a problem that should concern us all.
Which organizations should be concerned?
While any organization can be targeted, those most at risk would be those whose data footprints indicate vulnerability and value to an attacker. Social engineering happens because publicly available data indicates to a bad guy that there is an economic incentive to go after a target. If that target is also data-rich, then this provides both opportunity and motivation for a social engineer.
Traditional cyber security prioritizes financial systems as well as an organization’s “crown jewels”—intellectual property, business plans, deal memos and contracts, and other material of value that could be resold (for example, to the cyber criminal’s client), used to extort ransom payments, destroy reputations, or otherwise harm the organization.
Every organization should consider all of its operating and information systems, as well as financial and accounting systems, as attractive targets. Vendors and service providers in the supply chain as well as affiliates and business partners can expose the organization to social engineering attacks. Any party that the organization pays funds to or receives funds from, or even communicates with, can create exposures.
Organizations that operate in one of the 16 sectors designated as part of critical infrastructure by the US Cybersecurity and Infrastructure Security Agency (CISA) should be especially concerned. That designation means that the organization faces a specific set of requirements, which include disciplined cybersecurity practices. It also implies that organizations in those sectors may be particularly attractive targets, particularly for ideologically motivated attackers.
Which individuals should be concerned?
Everyone employed by an organization in any capacity, internally or externally, as well as anyone doing business with an organization, should be concerned about social engineering. That is especially (but not only) true of individuals with access to an organization’s systems. Anyone whose personal and work information is exposed online, whether it be on social media, data broker sites, breach repositories, corporate or personal websites, or elsewhere, is vulnerable since the fuel for a social engineering campaign against them is already available to an attacker.
Senior executives, board members, and key clients, customers, and investors of an organization should be especially concerned. Those individuals, (known as “whales” to attackers), are often impersonated by cyber criminals to obtain sensitive information from targets based on the senior person’s position and authority. Also, because attackers often focus on wealthy individuals and their assets and those of their families, senior leaders can be attractive targets apart from their role in an organization.
Ultimately, no one is immune to social engineering. Even the most wary employees, even professional social engineers and security specialists, have been successfully tricked by a clever scam crafted from their own data. While cybercriminals may not be “smarter” than their targets, they are engaged in cybercrime full-time. That makes them as expert and sophisticated in their chosen field as legitimate professionals are in theirs.
Why do current solutions fail to stop attacks?
Traditional “moat-and-fortress” defenses don’t work against social engineering because the technique is designed to overcome those defenses. Hardened infrastructure is easily bypassed if an attacker can successfully trick an employee into granting access. Moreover, social engineers use data on the targeted person—and often on a party trusted by that person—to craft approaches that will appeal to, and convince that specific person, and this data lies outside the control of conventional cybersecurity.
The organization and its cyber security staff are not really in a position to address “the weakest link” in the defense against social engineering attacks—the individual. Attackers target and approach individuals when they are either on or off the job or on their company-issued or personal devices. And they do this based on information on that individual that’s “out there” in cyberspace.
Cyber security professionals have very little control over either the individual or the publicly available or easily accessible information on the individual, particularly compared with the control they have over the internal IT environment. Indeed, that is exactly why social engineering is utilized and why it is so effective.
Most organizations rely on training employees to recognize attempted social engineering attacks. They also work to create awareness about these attacks in general, as well as awareness of specific new attacks. For example, the cyber security staff will flag suspicious emails that are going around and warn employees not to click on links or open attachments. These efforts can extend to customers, suppliers, and other parties, but often do not.
While training and awareness are a part of a good defense against these attacks, they are only part of that defense—and, historically, not wholly successful. In-person and video training may be informative, but often fails to engage people intensely and personally enough. Training also has a decay factor, particularly if done only during onboarding with occasional updates or refreshers. And pointing out suspect emails or scams generally occurs after those emails have done damage. Further, while cyber security professionals work hard to keep everyone informed and aware, they are notoriously busy making system improvements, implementing special projects, and responding to incidents and breaches.
How should you evaluate potential solutions?
Any potential solution for improving the organization’s defense against socially engineered attacks should address the root cause—the information that attackers use to select their targets and design their approaches. That’s because personal information enables socially engineered attacks.
The solution should also engage individuals who could be targeted and keep them engaged in an ongoing, easy-to-use manner. That would address the major shortcoming of training, which should remain in the mix, but not be the major defense against these attacks.
A tech-based solution to this human-behavior problem would be ideal. The technology solution should address the root cause, not rely on attempts to “screen” emails or texts, and readily integrate with existing IT systems.
The solution should also respect the individual’s privacy and autonomy. An organization in a free society cannot “control” an employee’s or other party’s available information or online and social media behavior. Yet it can definitely provide support for practices that lower the individual’s exposure as a target of organizational and personal attacks.
The solution should also be easy for the cyber security staff to understand, implement, maintain, and communicate throughout the organization. As noted, cyber security staff have their hands full as it is, and no solution that fails the ease-of-integration, ease-of-use test will be practical and sustainable.
In sum, the solution should address the root cause, be engaging and tech-based, respect individual privacy, and be easy for security staff to deploy and maintain.
Of course, the solution should also be effective in reducing or eliminating social engineering attacks on the organization and its stakeholders.
How Picnic works and why it’s different
The first technology platform capable of addressing the social engineering problem holistically and at its source was created recently by a team of specialists with backgrounds in human intelligence, mathematics, and engineering, whose company name is Picnic. The name Picnic is derived from an old IT security acronym that stands for ‘problem in chair, not in computer.’ Since social engineering targets people in order to bypass technical controls, the company based its name on this saying but has reframed it with a positive spin as ‘Protection in the Chair, Not in the Computer.’
Picnic’s platform works by emulating the way an attacker conducts reconnaissance on the publicly available data of companies and their people, exposing and flagging the information that an attacker would likely use in a social engineering attack, and providing users with the capability to either remove or neutralize that information. If any employees in an organization have exposed credentials on dark web for instance, or have a digital footprint that is attractive to social engineers, or are otherwise high-value targets for social engineers, Picnic’s technology automatically recognizes this and includes built-in tools to remediate and reduce a company’s social engineering risk at scale.
SANS FIRST LOOK WHITEPAPER ON PICNIC

Jeff Lomas of SANS discusses the importance of knowing your attack surface from the outside in and how Picnic can help organizations tackle the largest problem in cybersecurity—social engineering.
To protect individual privacy, the platform consists of two applications that work together. One of these is called ‘Command Center’ and is used by enterprise security teams, while the other is an employee-facing personal dashboard called CheckUp. The way the platform is set up allows security teams to know where their company’s social engineering risk resides and to take remedial actions without viewing any sensitive non-public personal information of employees.
It is the employees themselves who actually see and manage their own exposure through their own personal dashboard. In contrast to traditional awareness training, employees using CheckUp can see the very real and specific risks that their exposed information poses to them personally, and by extension their company. They are also provided with active learning on cyber hygiene best practices and the technological means to reduce their social engineering risk by controlling their digital footprint.
What makes this application particularly engaging for employees is that it gives them visibility and control over their digital footprint that was not possible before and protection against social engineering that extends across the work/home boundary. Employees can even broaden their protection to their households with family invites. Moreover, since online data exposure changes constantly, the CheckUp application continuously monitors users’ footprints for any changes and alerts them of new risks. Importantly, Picnic’s platform also passes the ease of use criterion necessary for a viable solution to the social engineering problem, as this customer story illustrates.
Ultimately Picnic’s solution works to combat social engineering by treating the public data of an organization and its people just like a social engineer does—as a human attack surface with vulnerabilities to exploit. In providing companies with the capabilities to see and eliminate their public data vulnerabilities proactively, Picnic delivers a verifiable reduction in an organization’s human attack surface and with it a dramatically reduced social engineering risk.
How to protect your personal information to prevent social engineering
For individuals without access to Picnic’s platform who want to reduce their attack surface, there are several effective steps that can be taken. To get an initial idea of some of your exposed information and how a social engineer would most likely contact you, you can get your free report here: https://checkuplight.getpicnic.com/.
- When online, use a “secure by default” technology such as Cloudflare or Google DNS. This should be setup on personal devices and your home network. Remove any personal information, such as birthdays, home addresses, city and state, middle name/initial, phone numbers, geolocation information, and vacation plans from all social media accounts, and only connect with people you know. Review your privacy settings regularly and always set them to the highest level possible.
- Whenever possible, establish and use online pseudonyms and related emails to shield your identity and use different personalized images for different platforms. Avoid posting job titles that draw an attacker’s attention, remove old posts and pictures, and delete any old or unused social media or e-commerce accounts. Have your family members apply the same practices. If you own a blog or website, go to your domain registrar and see what options they provide to make your WHOIS information private.
- For other information that is available online about you, search yourself to see what is out there about you and your family: “search your address in quotes”; “search your name in quotes”; and “search your email in quotes.” Submit removal requests through Google to delist links that contain personal information. In addition to Googling yourself, run your name on data broker sites, such as mylife, peoplefinders, searchpeoplefree, fastpeoplesearch, radaris, and USphonebook. Contact each data broker and request your information be removed. Repeat the process regularly for you and your family members.
- To know if your credentials have been involved in a breach, enter your phone or email into https://haveibeenpwned.com/ to see your exposure. Make sure any breached credentials are not being used on your personal or corporate accounts. To protect against credential compromise, use a password vault, never reuse the same password on different accounts, and use strong passwords and multifactor authentication (MFA) whenever possible.
- Lastly, use spam filters for email and download an anti-phishing browser extension. If you do get a suspicious email, don’t click any links and never download or open a suspicious attachment. Hover your mouse over the link to reveal the website address. If you accidentally click and are prompted for login credentials, stop there.
A skilled social engineer doesn’t need much personal information to do damage, but by adopting these practices, you can significantly reduce your visible attack surface and your risk for social engineering.
Become a Subscriber to receive timely articles on human-centric security issues: