PRIVACY AS A MANAGED SERVICE
Continuous and automated data broker takedowns.
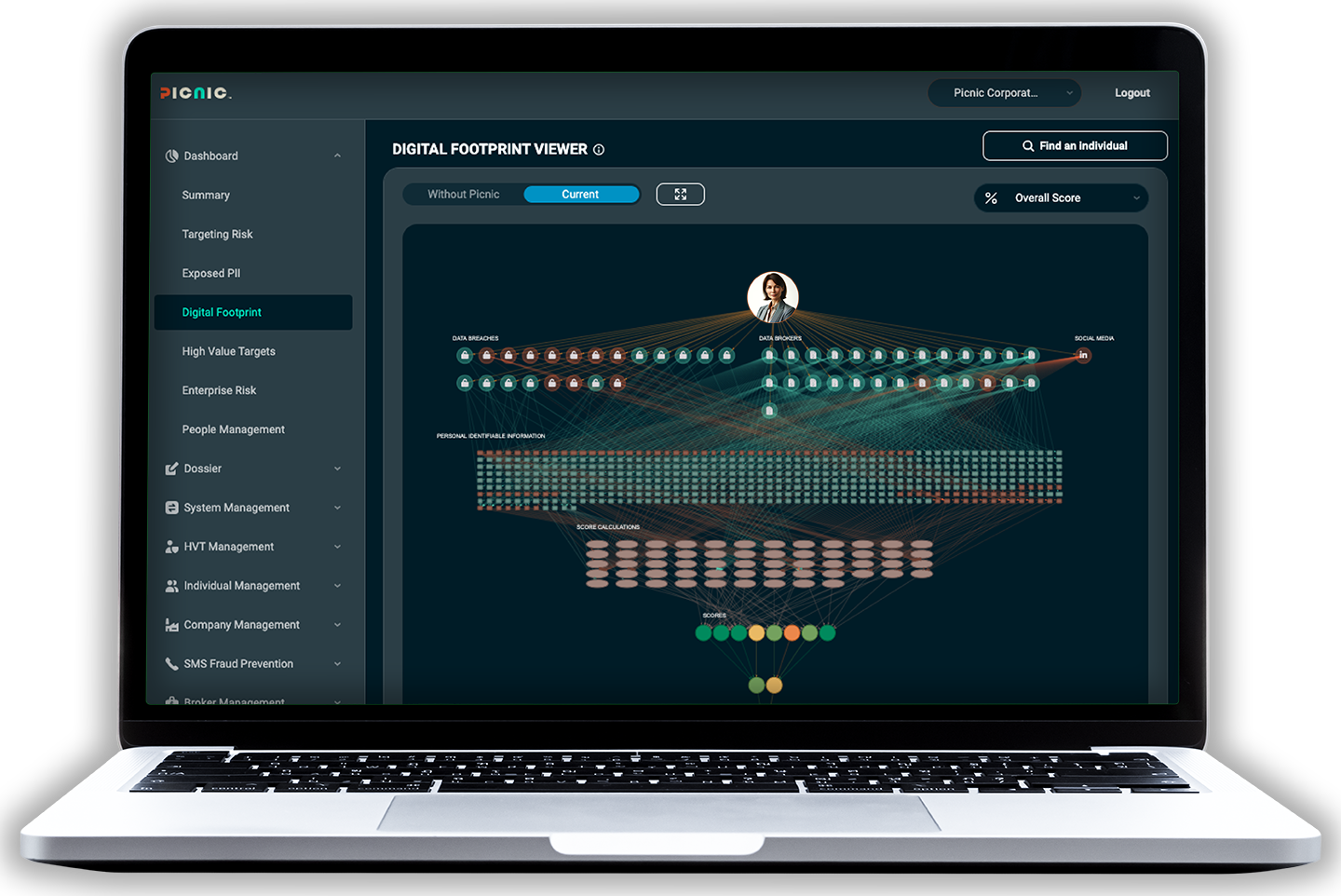
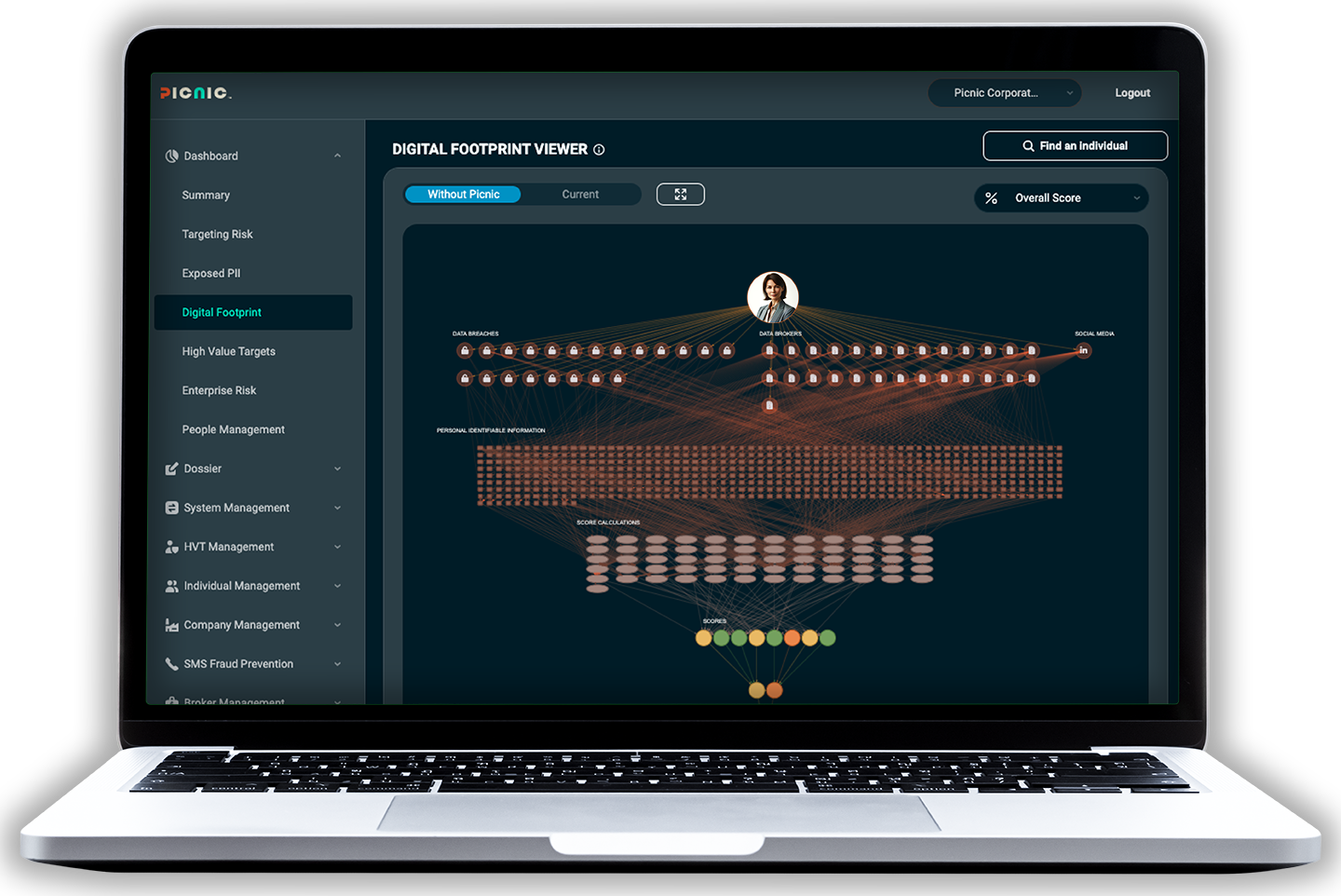
DIGITAL EXECUTIVE PROTECTION
Protect Executives and their Families
Protect from deception, impersonation, harassment, coercion, and other threats with zero effort. Picnic offers a managed service that combines the unique technical capabilities of its automated platform, specialized knowledge of how attackers conduct reconnaissance and gain initial access, and proactive remediations to protect those individuals in your organization who are at high risk of being targeted or exploited by threat actors.
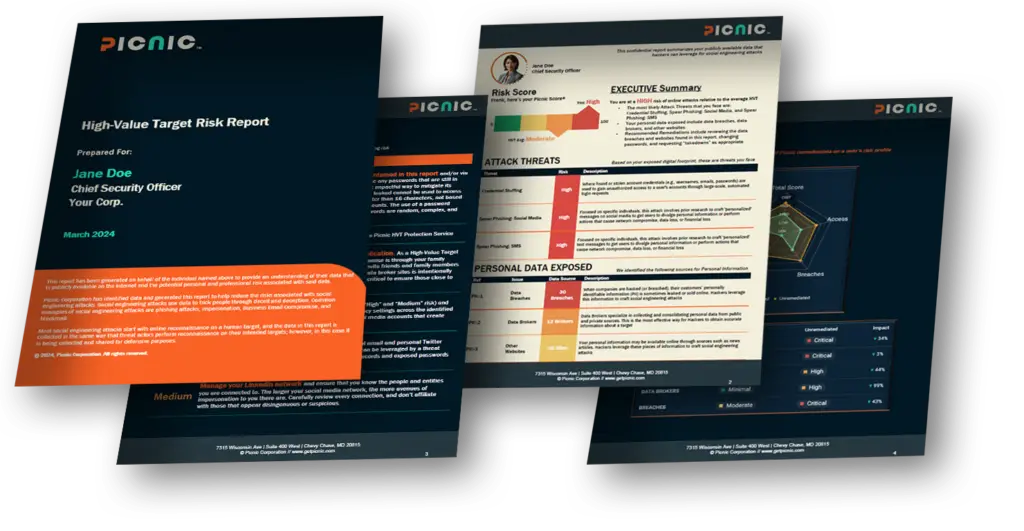
Standard Features
- Continuous monitoring of the complete data broker footprint and automated takedowns (US and international coverage)
- Dark web monitoring for exposed passwords related to current and former work identities
- Dark web monitoring for exposed passwords related to personal identities
- Dark web monitoring for exposed passwords related to corporate service accounts and domains
- Automated detection and remediation of impersonation on social media
- Automated detection of misconfigured DMARC, DKIM, and SPF records for professional and personal websites
- Ransomware, malware, and virus protection for personal devices + laptop-sized Faraday bag
- Real-time messaging about external footprint changes and related risk via email, Teams, or Slack
- Comprehensive individual risk report
- 1:1 consultations based on unique needs
- Up to 10 invitations for extended protection coverage to family members
- 24/7/365 incident response support
- Security team access to an online portal to visualize threat exposure and completed remediations
Add-on Features
- Breached credential reuse protection via API or native Active Directory integration
- DM Defender anti-smishing mobile app (beta)
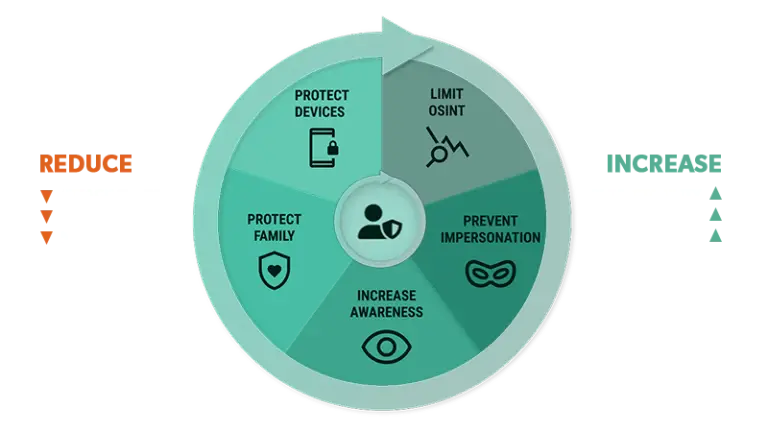
Picnic delivers security outcomes
DIGITAL EMPLOYEE PROTECTION
Deliver Privacy as a Benefit to Protect your Business
Highly accessible employees can be tricked or coerced into performing actions that put the organization at high risk of compromise, like enabling initial access to threat actors or sharing confidential information. Picnic offers a win-win scenario by protecting the organization from social engineering while offering a free perk to employees to reclaim their privacy online.
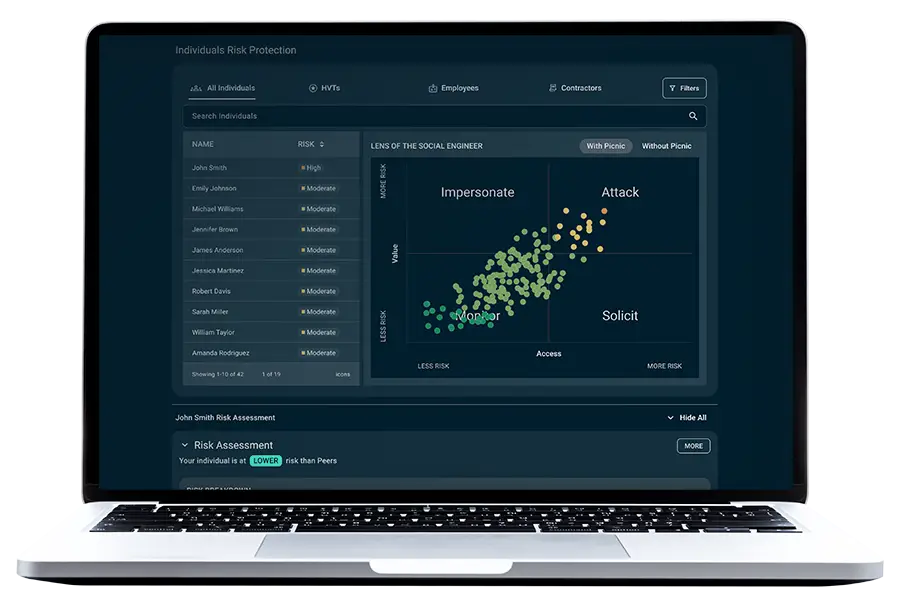
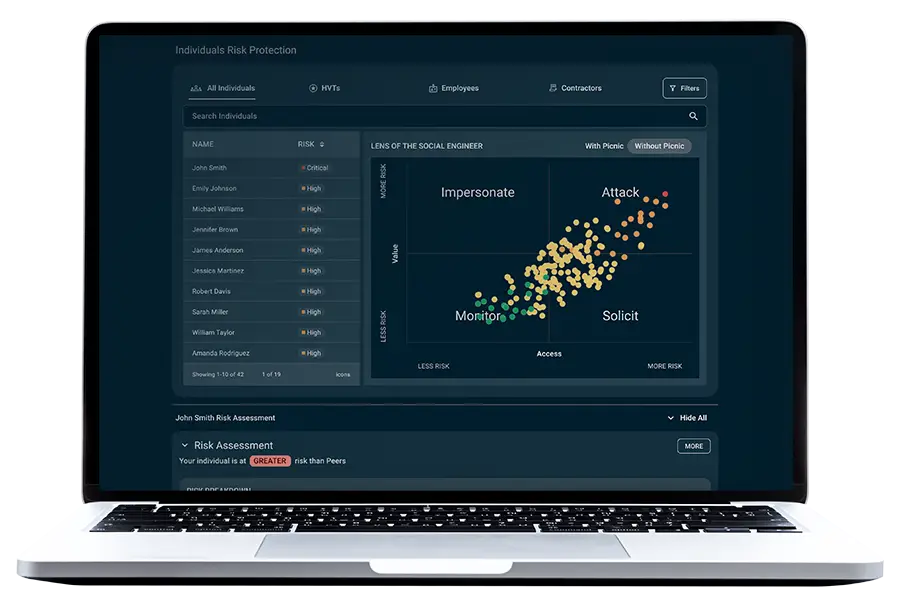
Standard Features
- Continuous monitoring of the complete data broker footprint
- Automated takedowns of data brokers
- Domestic (US) data broker coverage
- Dark web monitoring for exposed passwords related to current and former work identities
- Dark web monitoring for exposed passwords related to personal identities.
- Dark web monitoring for exposed passwords related to corporate service accounts and domains
- Real-time messaging about external footprint changes and related risk
- Multiple ways to enable employee opt-in
- Security team access to an online portal to visualize threat exposure and completed remediations
Add-on Features
- Customized individual risk report
- Invitations for up to five family members to extend protection coverage
- Breached credential reuse protection via API or native Active Directory integration
- DM Defender anti-smishing mobile app (beta)
Picnic increases predictability, visibility, and control

Outcomes and Benefits
Preempt the single largest source of breaches
Secure work and personal identities, disrupt attacker reconnaissance and resource development, and protect your human element, business processes, and infrastructure.
Safeguard your people
Protect your executives, employees, and contractors from being targeted or exploited by threat actors.
Prioritize defenses
Fill a critical security gap with targeted remediations informed by relevant and timely human risk intelligence mapped to your workforce.
Personalize security coaching
Tailor education to combat real-world threats with data-driven, risk-based social engineering training and critical risk alerts.
Quantify and reduce human cyber risk
Know and communicate your progress with comparative scoring and reporting capabilities that facilitate sharing with stakeholders at all levels.
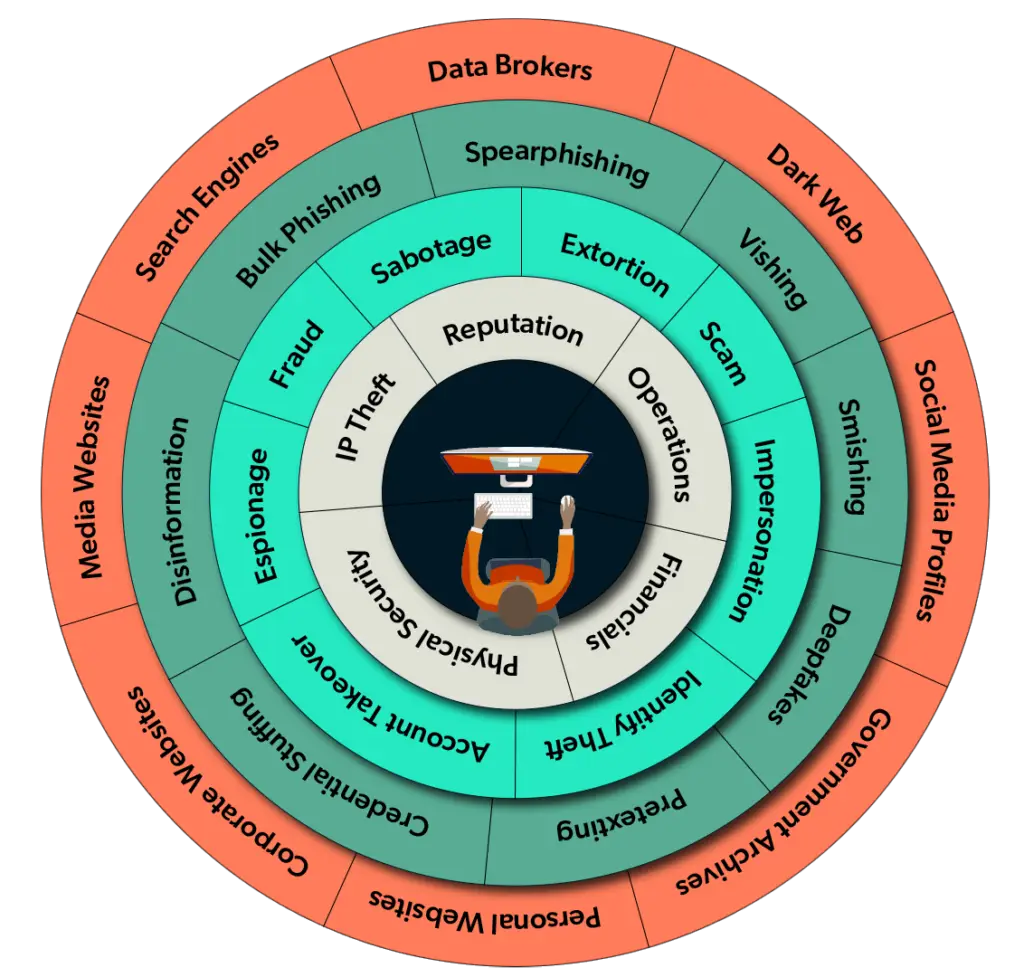
Service capabilities
If you want to learn about Picnic and how we deliver privacy as a managed service for enterprises, this is the webinar to watch. Matt Polak, CEO and founder of Picnic, explains the rationale behind Picnic’s approach to reducing human risk, shows you how threat actors conduct target reconnaissance and build dossiers to craft social engineering attacks, and gives you a short demo of the dashboard where customers can visualize risk and track measurable progress toward their security goals.