By Matt Polak, CEO of Picnic
Cyber threat intelligence indicates that there is a high probability of digital retaliation against Western companies and governments that have supported Ukraine or distanced from Russia. Russia has validated this intelligence and their cyberwar strategy is evident: they harvest personally identifiable information (PII) about individuals and use it to power social engineering schemes to conduct attack and compromise campaigns that cause damage, collect intelligence, and generate income.
Organizations that have cut (or iced) ties with Russia, or those supporting Ukraine, are most likely to be the direct targets of Russian cyber aggression and retaliation. There are three things you should know about how threat actors like Russia operate:
- Their #1 attack vector is social engineering.
- Their #1 target is high-value employees.
- Every attack begins with reconnaissance of public data footprints (i.e., OSINT data).
Unfortunately, existing controls are not likely to stop sophisticated social engineering attacks: training doesn’t work (people can’t be trained to spot these well crafted attacks), and technical controls like mail gateways and endpoint protection can be defeated with staged operations that identify (to evade) such technical controls.
In addition to the #shieldsup activities that are ongoing, below are some simple steps companies concerned about retaliation should take immediately.
What should you do
- Embrace the attacker’s mindset
- Identify your targets
- Remediate
- Repeat
1. Embrace the Attacker’s Mindset
Start by approaching this problem as the attacker. Ask yourself some key questions:
- What systems would I want to gain access to?
- What security controls, if exploited, would lead to catastrophic damage?
- Who has access—either to the systems themselves or to the controls?
- Who do you think would make the best target if you were the attacker? Why?
This last question is key and leads into the next activity: identify your targets.
2. Identify Your Targets
Make a list of your people as follows:
- Group 1: People (probably your C-Suite and Board) whose personal brands and reputations are intertwined with your company’s brand and reputation.
- Group 2: People who work directly with and support “Group #1”
- Group 3: People with privileged access to your “crown jewels”
- Group 4: People who work directly with and support “Group 3”
- Group 5: If not already considered, the people who have privileged access to your organization’s security controls
- Group 6: People who work directly with and support “Group 5”
I recommend putting these people into a spreadsheet for simple management, since you’ll want to capture some additional information on each one.
First, for person in each group:
- Add their LinkedIn profile (assuming they have one) to your spreadsheet
- Add their work and personal (if available) emails to the spreadsheet
Create a few columns on which you can track some basic data about each person with a simple Yes or No.
For their LinkedIn profile:
- Does the person list a specific geography where they are located?
- Does the person list anything in their profile that would suggest they would be an attractive target? Words like “administrator” or listing technologies or processes they are responsible for are dead giveaways.
- Does the person list any contact information on the page?
For their work and personal emails:
- Run through whatever breach repos (sites on the public, deep, and dark web where people’s usernames, passwords, and other personal information are stored and sold) you have access to and denote the quantity (as a count) of cleartext credentials available for each person.
When you are done, your spreadsheet should look something like this, sorted by seniority:
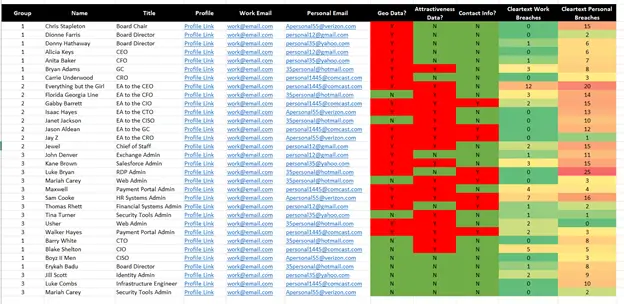
You can use some basic approaches to analyze this kind of data that leverages your knowledge of your company and its security practices, as well as the questions you asked yourself upfront when you thought like the attacker.
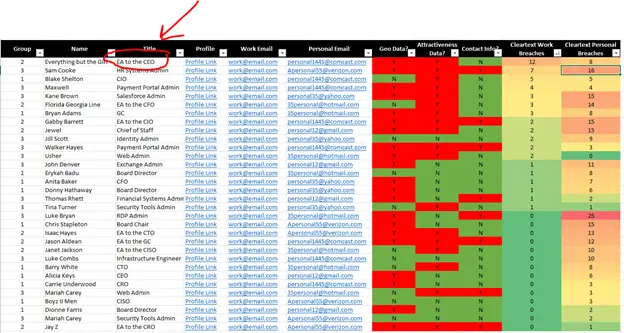
For example, as seen above, you might decide that people with the most amount of breaches in their work emails are important to triage first. In this view, the EA to the CEO is most likely to be targeted, so you might increase sandboxing for their account, have a direct 1:1 security coaching session with them, and make some reasonable requests to modify personal data to neutralize oversharing in social media. At a minimum, you should make sure that none of the cleartext credentials you found are being used in your company’s infrastructure, and ideally not used in an employee’s personal life. After all, attackers want to find the easiest path in, and it’s usually smooth sailing into unmonitored personal email and interconnected social media.
If you want to apply more analysis, you could associate a score of 1 point with any “Y” and weight everything equally. Doing so would yield a target list that looks quite different and makes your RDP Admin (yikes!) to the #1 target for attack:
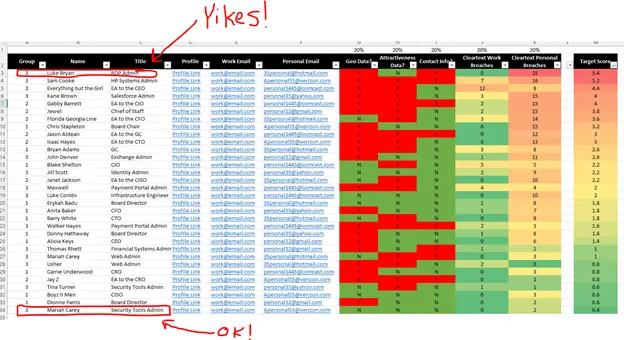
Organizations have limited human analyst resources capable of solving problems that computers can’t solve, so knowing where to invest valuable staff resources is critically important in our current elevated threat environment.
There are many approaches that can yield valuable insight into how to secure your organization based on the view of the attacker. Remember, the way the attacker prioritizes their targets is based on reconnaissance of public data. Seniority is a useful metric, but it’s only one consideration. Oftentimes it is those people who are accessible rather than valuable who are the first line of attack for hackers who seek to leverage credential escalation and lateral movement. For example, the executive assistant to the CTO could be easily overlooked by an internal security organization, but someone in this role likely has shared access to certain systems that are sensitive, and therefore would likely be a prime target for an attacker.
3. Remediate
Now that you know who is most likely at risk, we recommend a quick scrub of OSINT data to make your team harder to target. In order of priority:
- Passwords. Confirm that all cleartext credentials are not in use and ideally banned from your systems and also ask employees to confirm they are not using these credentials either.
- LinkedIn. Go back to the list of words or phrases that powered your evaluation of LinkedIn. Send a quick email to your team asking them to change or remove these words with an explanation as to why. (see “resources” below for a sample communication)
- Data Brokers. Find and remove data brokers, which are an easy source for threat actors looking for PII on your employees. To do this, run a series of Google searches for the people in your list such as: “Full Name” + “work email”; “Full Name” + “personal email”; and “Full Name” + “home address”. Results will commonly include data brokers such as Whitepages, Spokeo, MyLife, and ZoomInfo. These data broker sites support removal requests, though the process can take time and is not uniform. If you want help with this, please contact me or comment.
4. Repeat
This type of exercise should be run continuously in good times and in bad. Digital footprints and employee populations are in constant flux, and so are attacker motives and methods. Building capacity for this type of capability will help build a security culture and create good operational security practices that should be the backbone of any security strategy.
Remember, hackers scout your organization to find an easy way in so they can compromise your people, your company, and your brand (in that order).
Picnic solves this problem at scale, so if you want to learn more about how to come upstream of the attack to stop hackers, please get in touch with us to schedule a demo.
Resources
After reducing the attack surface of the human, the next step would be to consider something like what has been proposed by Krebs Stamos Group, who provided helpful advice for those exiting the Russian market (or icing) ties with Russian connected organizations.
Sample Communication
[EMPLOYEE],
In light of [COMPANY’s] position in the global market and recent actions with respect to Russia, we conducted a threat assessment to identify ways to protect our highly valued employees like you from hackers who might retaliate against [COMPANY].
Hackers are targeting the personal lives of employees to gain access to company systems, so it’s important we take this threat seriously for both the company and you.
Based on the threat assessment we conducted, we are asking employees with the following information in their LinkedIn profiles to change or remove it.
Please remove the following references:
- System Name 1
- System Name 2
- System Name 3
We believe that by removing these references it will make you less likely to be the target of malicious activity, which will make you safer online both at work and home.
This small change will make a big difference for you and your colleagues.
Thank you for your help,
[NAME]