PRIVACY AS A MANAGED SERVICE
FOR THE ENTERPRISE

Picnic is the only digital privacy service purpose-built for the Enterprise, providing a turnkey managed service for reducing employee PII on the public web.
PICNIC FEATURES & BENEFITS
- Picnic is a fully automated service
- Purpose-built for the Enterprise
- No integrations required
- No effort required by the security team
- No effort required by employees
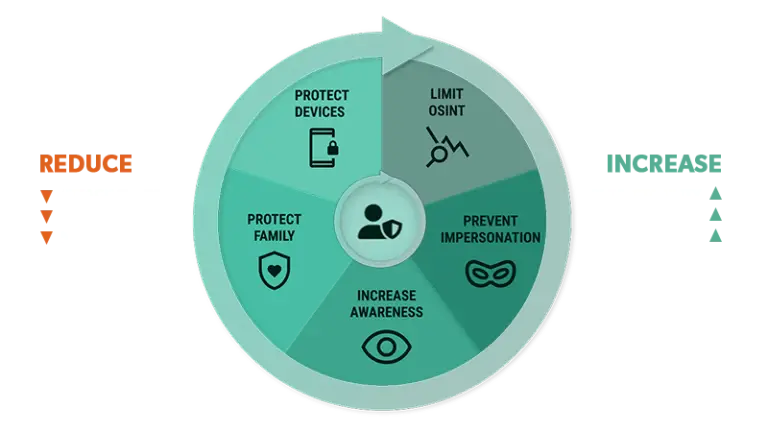
- Continuous data broker removals
- Dark web privacy monitoring
- Social media privacy and impersonation protection
- Family privacy protection at no additional cost
- Device privacy and protection
TESTIMONIALS


Social engineering is a key and growing threat to industrial organizations and Picnic offers important innovations to help the community strengthen its defenses. Picnic’s team understands how threats perform reconnaissance and initial targeting against companies and has built a privacy-forward platform for organizations looking to strengthen their cybersecurity.


As security professionals, the more that we can do proactively, the better. Many of the tools we have are reactive and happen after the fact. The less noise I have in my environment, the fewer things I can get upfront before I have to react to them, the better. Picnic plays in that space.


Everyone knows the human element is the single largest attack vector and security risk. Picnic is the first solution I’ve seen that prioritizes who inside the organization will be targeted and how based on human attack surface data. I believe Picnic changes the game for security teams.


One of the things that made Picnic attractive to us was the ability to make security personal for folks.


Picnic means high value, low friction, and acceptable cost. From easy uptake to easy execution, it has been fantastic.
PICNIC ADVISORY BOARD













Guide for Choosing the Right PII Removal Service for your Business
Avoid pitfalls when selecting a PII removal vendor to protect executives and employees against physical and cyber threats. It includes a Decision Checklist with recommended questions to ask when comparing vendors.
